Configuration of the Captive Portal on pfSense with FreeRADIUS
Configuration of the Captive Portal on pfSense with FreeRADIUS
🙋♂️ Welcome to this report where I will guide you through the process of configuring a Captive Portal on pfSense using FreeRADIUS.🙂
Overview
📋 Table of Contents
Introduction
A Captive Portal is a powerful tool for controlling network access, and when combined with FreeRADIUS, it offers robust authentication and authorization capabilities. Whether you’re setting up a network for your company or for personal use at home, this method provides a reliable solution.
Throughout this report, I’ll provide detailed step-by-step instructions accompanied by screenshots, so you can configure the Captive Portal yourself and enhance the security and management of your network, on pfsense using FreeRADIUS.
For this project i’ll be using 3 virtual machines
- Ubuntu 20.04 as a FreeRADIUS server.
- Ubuntu 23.04 as a client in the network (for tests)
- pfsense
Configuration
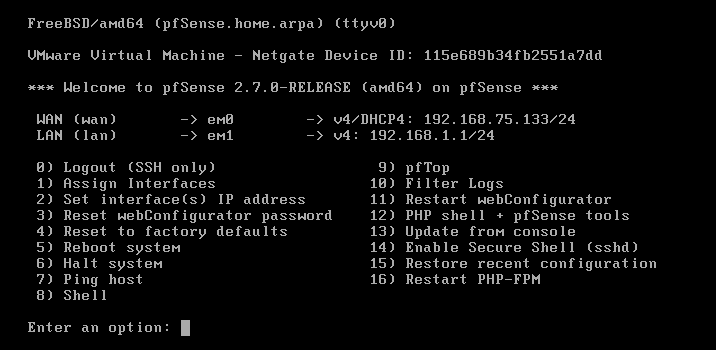
Step 1: Setting up pfSense
pfSense is an open-source firewall and router software that helps secure and manage computer networks. It’s easy to use and offers features like firewall protection, VPN support, and traffic shaping. It’s widely used in homes, businesses, and other organizations to enhance network security and performance.
For this step, I highly recommend watching this tutorial made by NetworkChuck. It covers all the installation steps of pfSense on hardware and as a virtual machine, and it is well explained. You can watch it by clicking here.
Step 2: Installing FreeRADIUS
At this step, I’ll be using two virtual machines. In the first one, I’ll install the FreeRADIUS server using the following commands:
1
2
3
4
5
6
7
8
# Update the package manager
sudo apt update
# Install FreeRADIUS
sudo apt install freeradius
# Start the FreeRADIUS service
sudo systemctl start freeradius
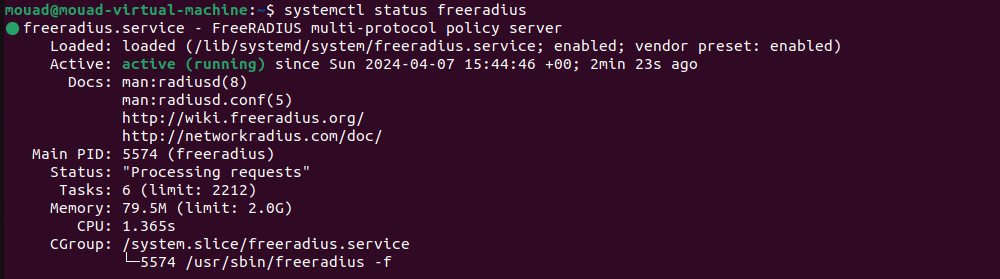
To check if everything went well, execute this command to see the status of FreeRADIUS:
1
sudo systemctl status freeradius
You should get a result similar to this one:
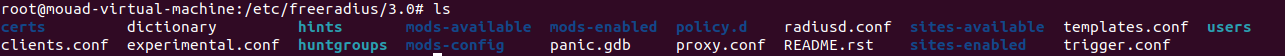
Now all the files we need are located in this directory: /etc/freeradius/3.0
the files we will work with are : users and clients.conf.
To help you understand their role, here’s a brief explanation:
📄users: The users file contains information about users authorized to connect to the network. It typically includes usernames, passwords, as well as attributes and restrictions associated with each user.
📄clients.conf: The clients.conf file specifies clients authorized to connect to the RADIUS server. It contains the IP addresses or IP address ranges of the clients, as well as shared keys used for authentication and authorization of RADIUS requests from these clients.
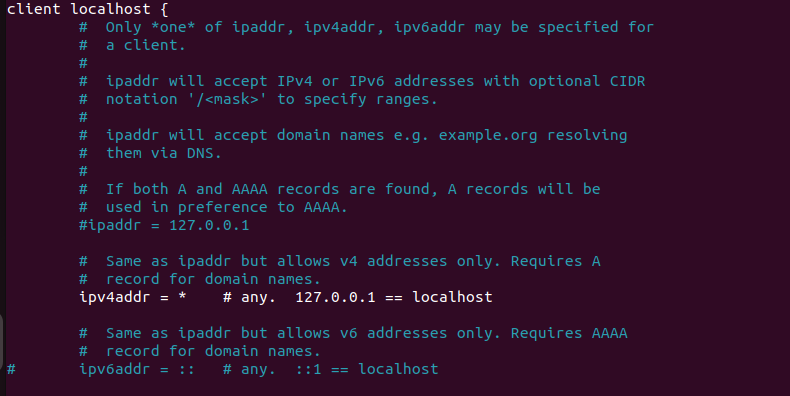
In the clients.conf file, here’s what you need to change:
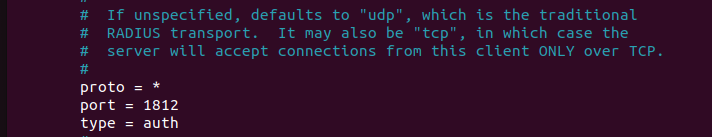
This line is meant to receive requests from all machines. However, to avoid any issues related to unwanted requests, you can specify the IP address of the pfSense machine, for example, a brute force attack.
To specify the protocol and the port. (Optional)
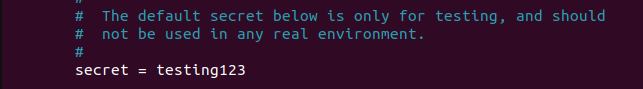
This line is very important as it will play a crucial role in the requests sent to the server, since each request must contain the shared secret.
In this configuration, the default secret is ‘testing123’. I will leave it as it is, but you can change it according to your preferences.
So far, the clients.conf file is well configured, you can leave the other parameters as they are by default.
Now, let’s move on to the users file.
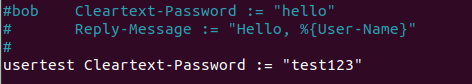
What’s flexible about the users file is that you can add accounts (usernames and passwords) anywhere because there are no specific fields. Just make sure to follow the syntax.
In this case, I configured the username as “usertest” and the password as “test123”.
After saving, you need to execute the following command each time to apply the changes:
1
sudo systemctl restart freeradius
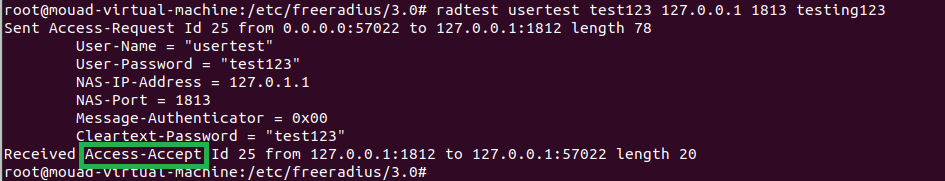
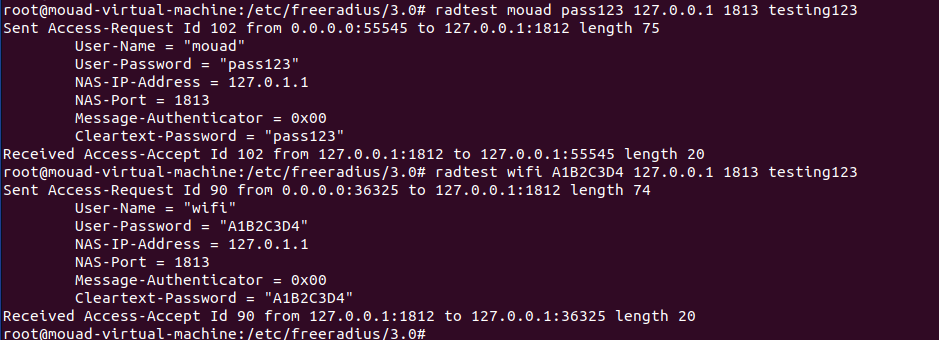
To test the proper functioning of all these configurations, you need to execute the following command:
1
radtest <username> <password> <@RADIUS_server_IP> <RADIUS_port> <shared_secret>
Since I’ll be using the command from the server itself, the command will be:
1
radtest usertest test123 127.0.0.1 1813 testing123
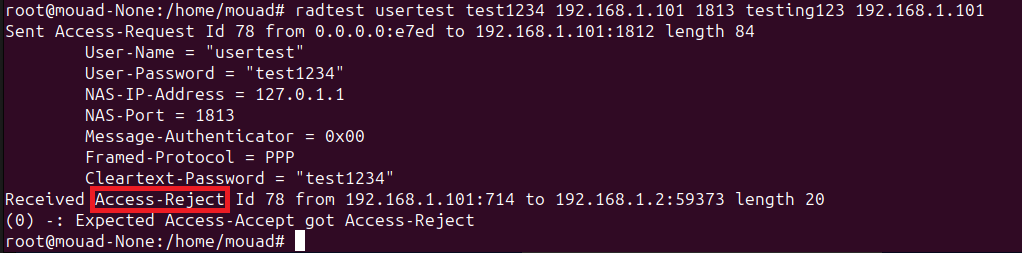
let’s try with a wrong password : 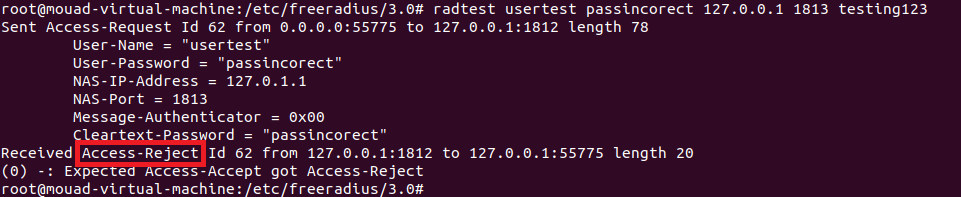
🙂Awesome, now everything is set up on the server. Let’s try to access it from another machine on the network.
For this part, I’m using another Ubuntu machine (Machine 2)
To use the client, you need to install freeradius-utils, which is the FreeRADIUS client, with the following command:
1
sudo apt install freeradius-utils
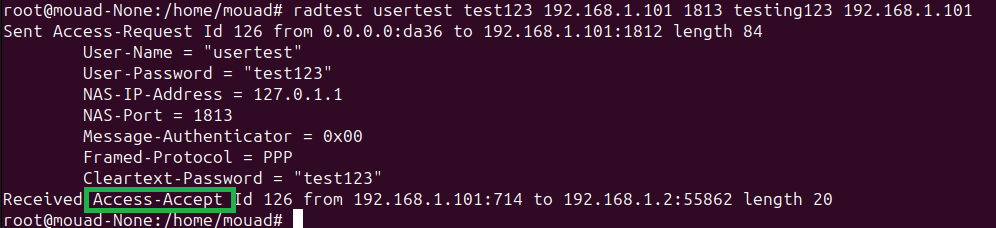
To test the proper functioning of the server, both machines are on the same network with the respective addresses 192.168.1.101 and 192.168.1.104.
Now with an incorrecte password :
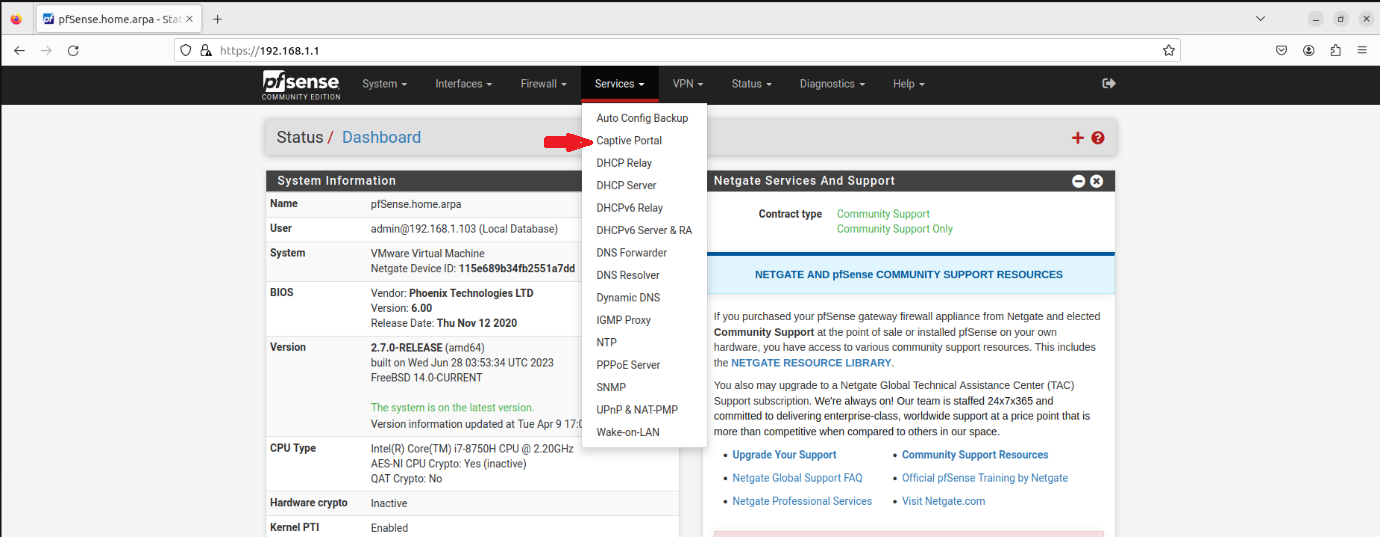
Step 3: Configuring Captive Portal
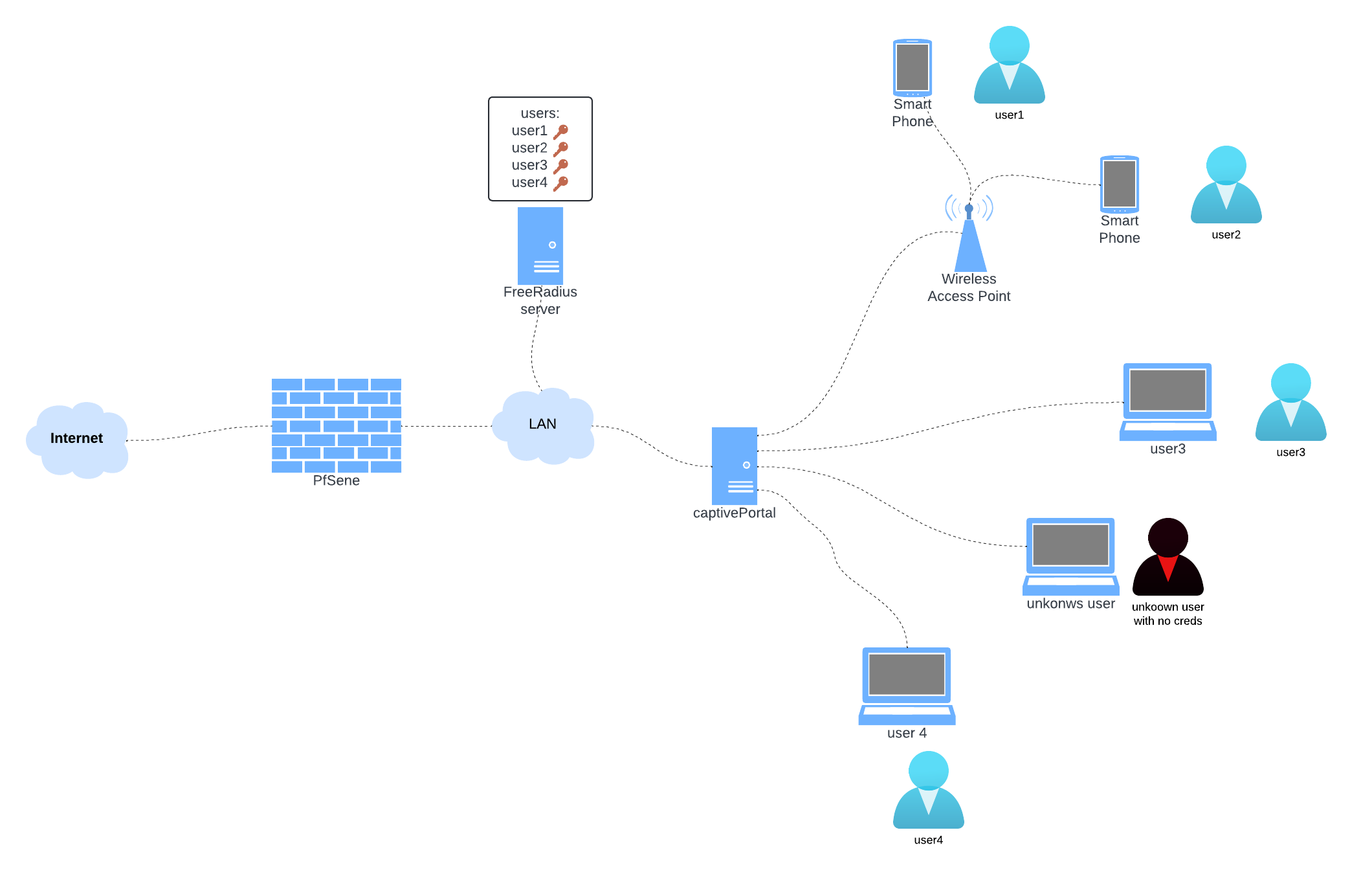
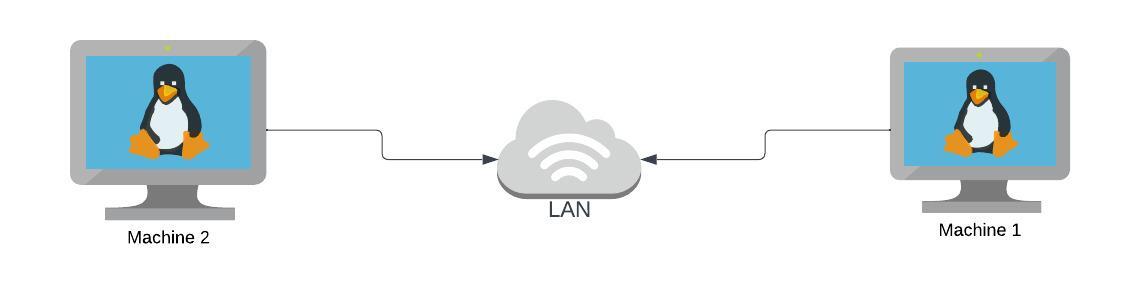
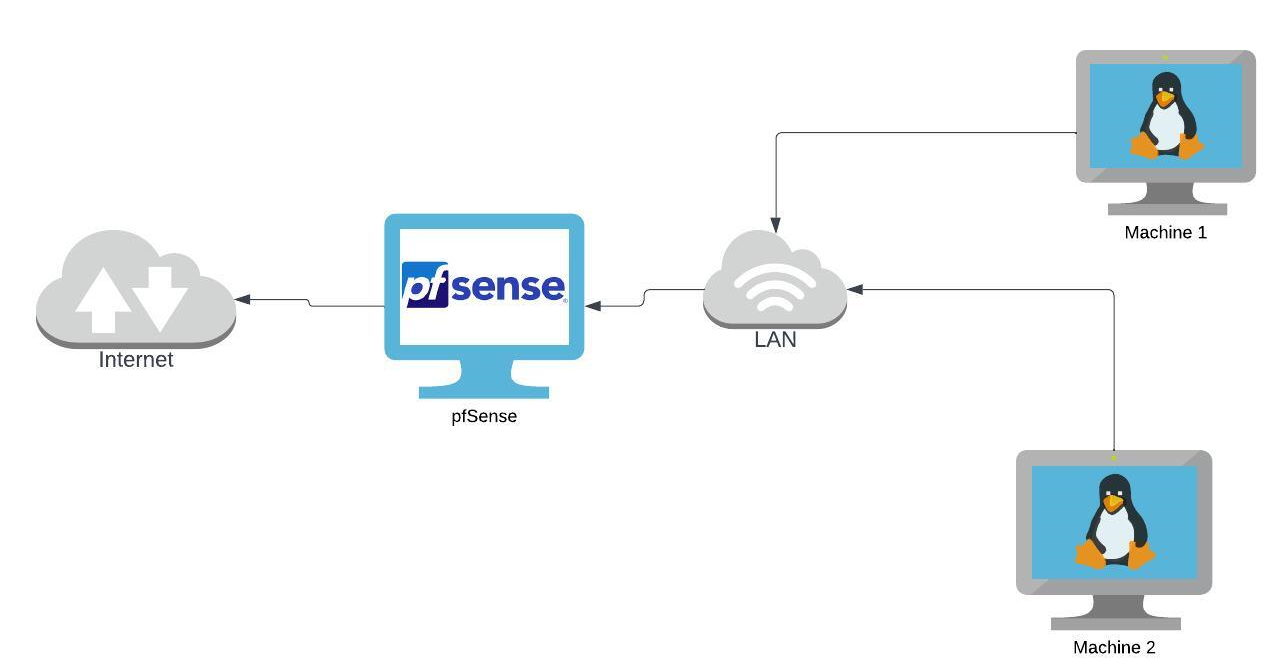
This is the architecture we’ll be working with right now.
Let’s proceed to link pfSense with the FreeRADIUS server we configured.
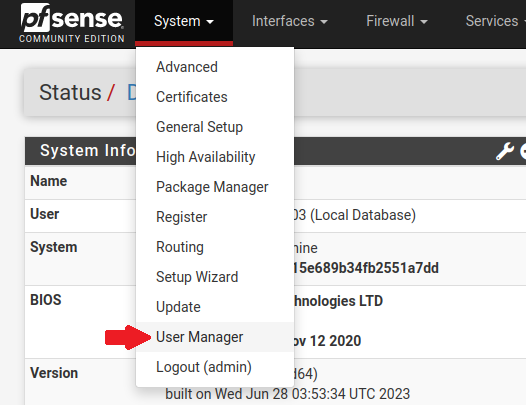
Let’s start by creating the FreeRADIUS user in the user manager.
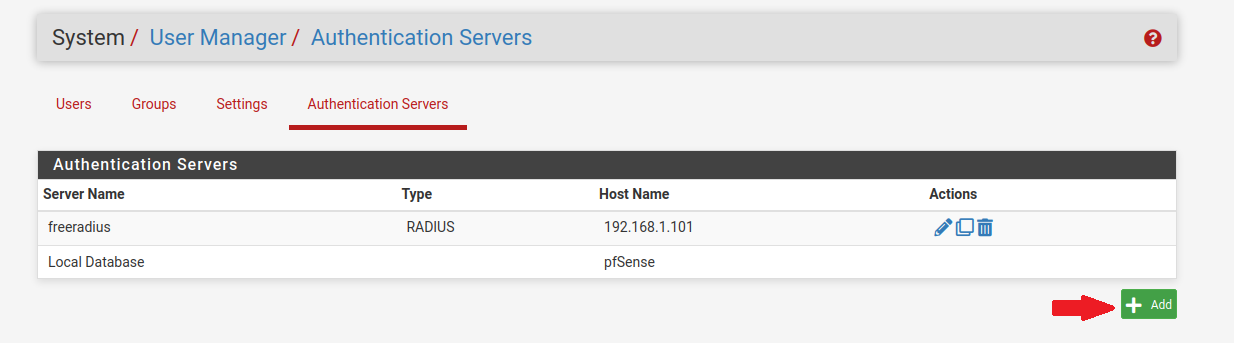
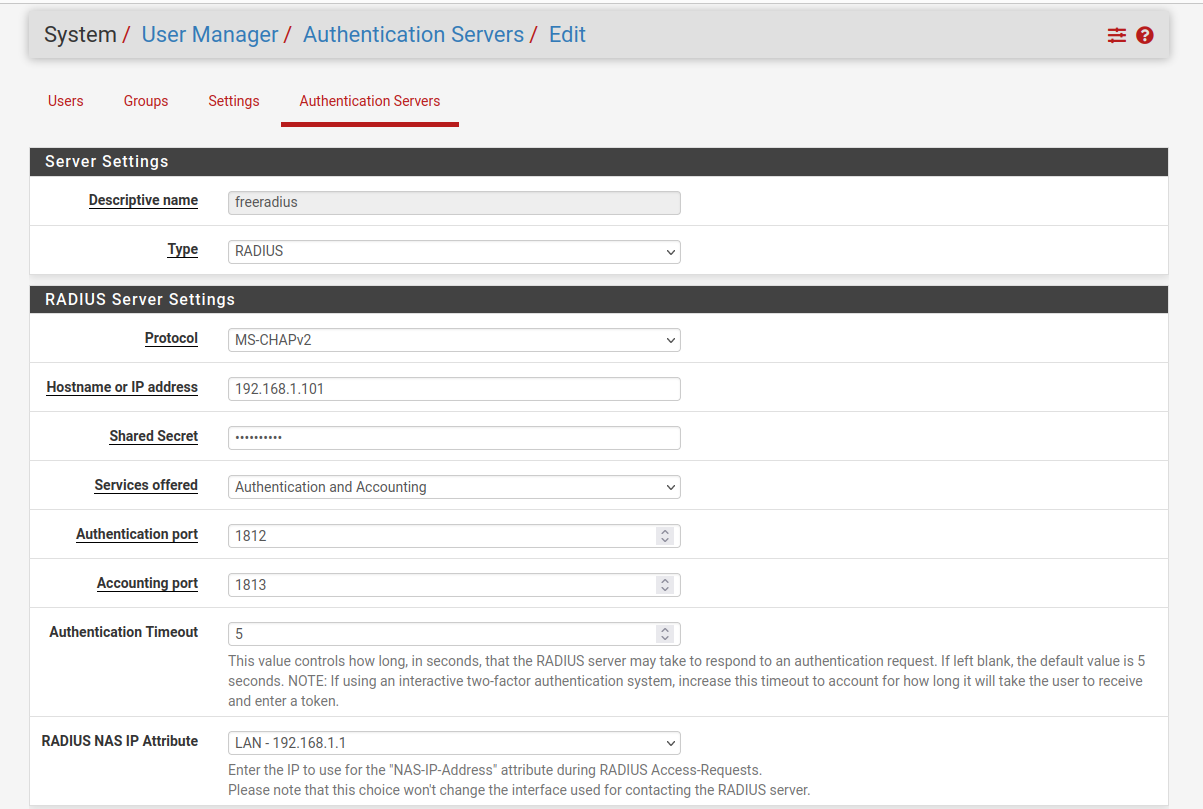
In the authentication server section, we will add a new user. I have already created the user under the name ‘freeradius’ :
Let’s create the FreeRADIUS user by providing the necessary information such as IP address, ports, and shared secret. In my case: the IP address of the Ubuntu machine is 192.168.1.101.
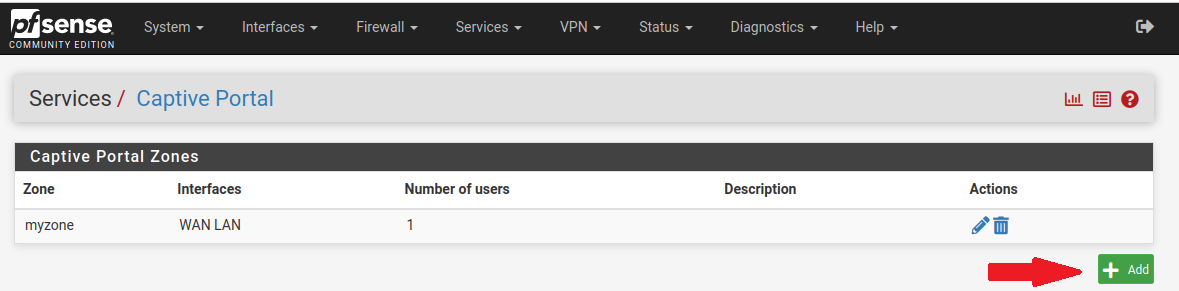
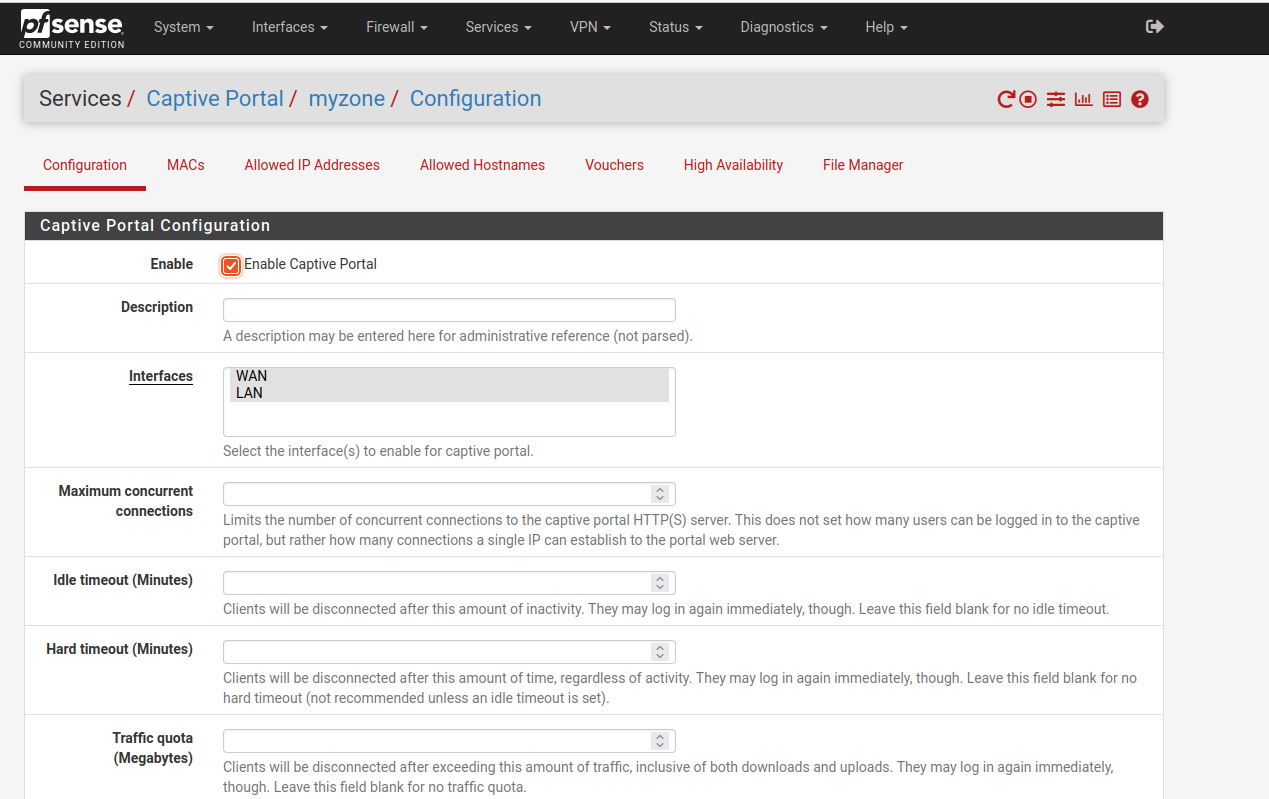
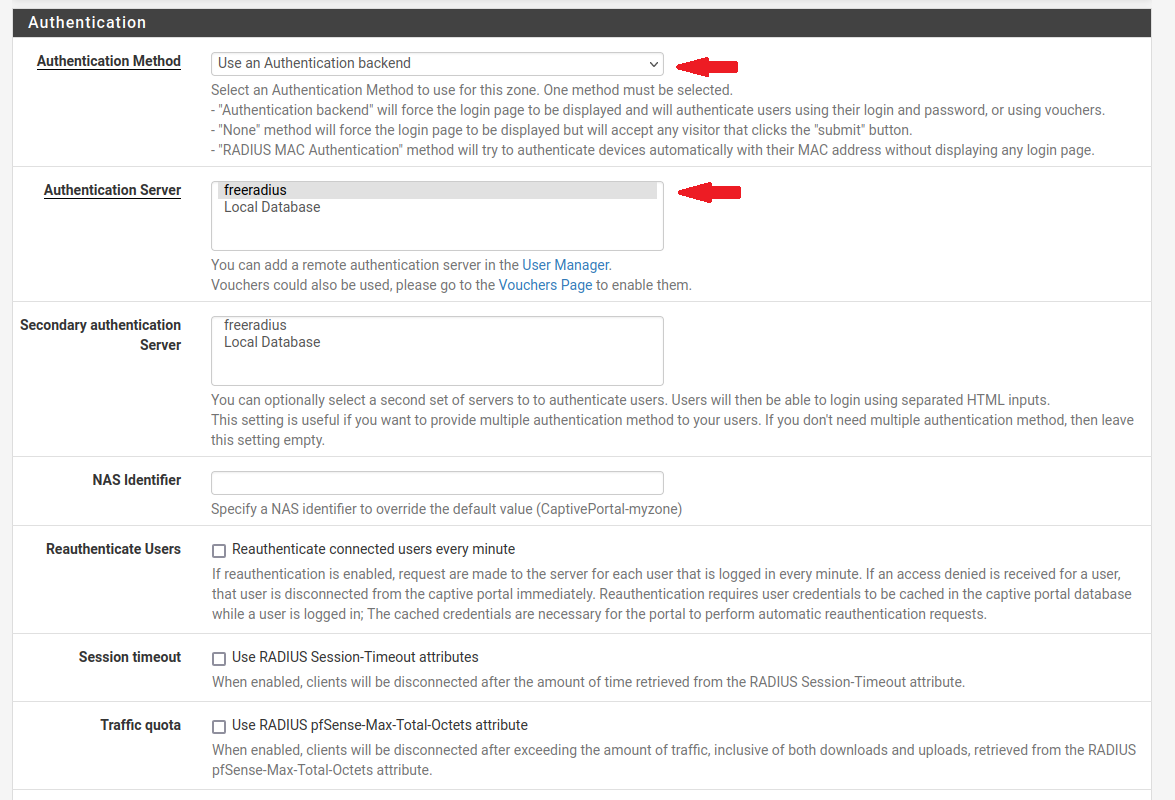
After configuring the FreeRADIUS user, we will now proceed to configure the settings in the CaptivePortal section.
Make sure you have all the necessary details and have configured the settings properly.
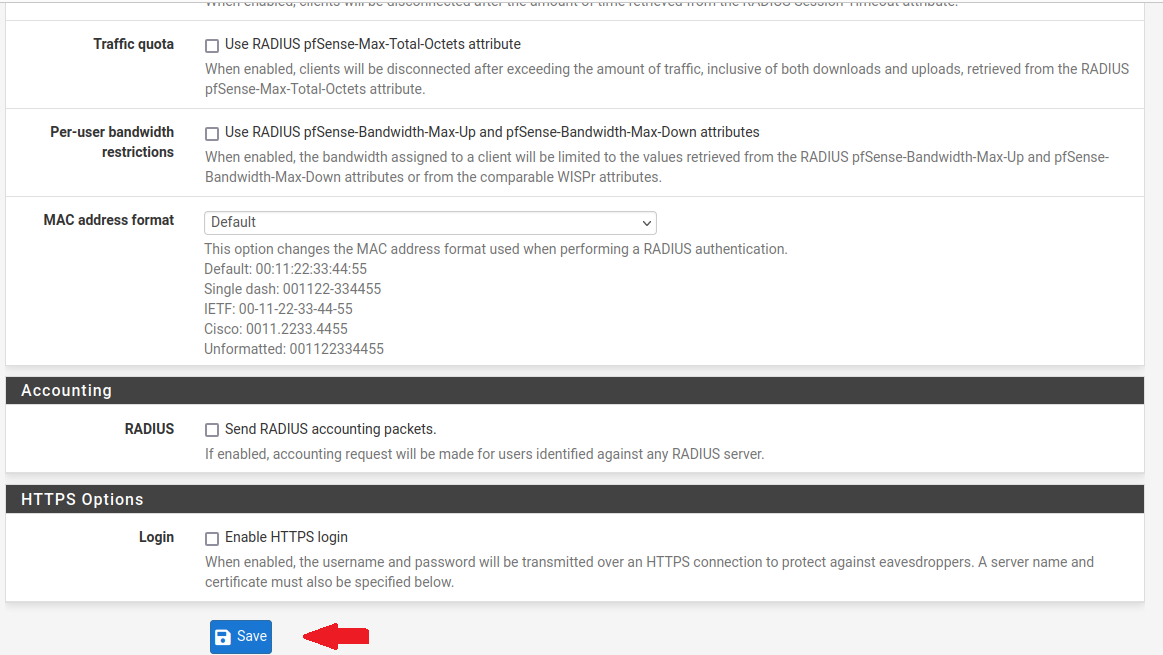
Now, everything is properly configured.
To connect to the Internet, valid credentials configured in the FreeRADIUS users file must be provided. For this :
If the browser does not offer the option to open the authentication interface, you can access it via the following link:
http://192.168.1.1:8002/index.php?zone=myzone
192.168.1.1 is the address of pfSense, and myzone is the name of the Captive Portal configuration.
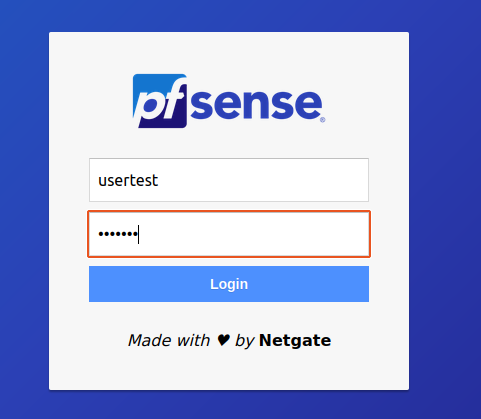
You should get this :
Let’s try using the credentials ‘usertest’ and ‘test123’.
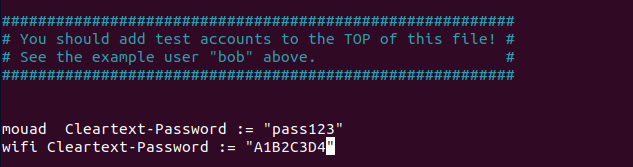
Now, I will add more usernames to the end of the file:
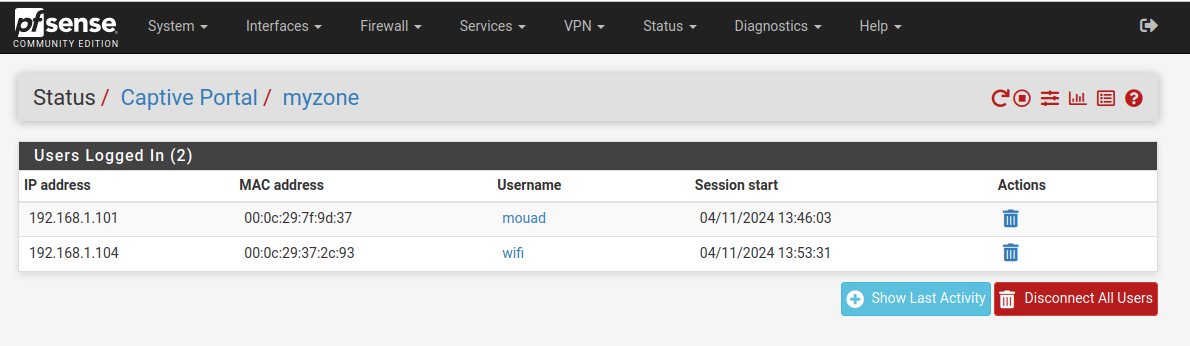
Regarding the status of the Captive Portal in pfSense:
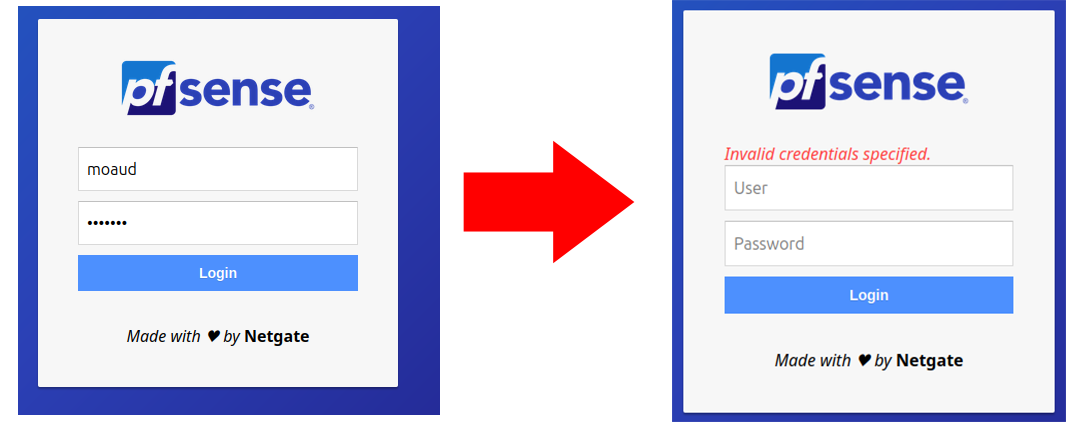
In the case of incorrect credentials, it returns this.
Conclusion
By following these steps, you can effectively set up and manage authentication and authorization for network access.
The integration of FreeRADIUS with pfSense offers a robust solution for controlling and securing network access, making it suitable for various environments, from small-scale home networks to large enterprise setups.
Overall, implementing a Captive Portal with FreeRADIUS on pfSense enhances network security and control while providing flexibility and ease of management.
✌️Thanks for reading.